 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
HamzInDaHouse
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 30 Nov 2024
Posts: 2
Location: Iraq
|
 Posted: Sat Nov 30, 2024 10:38 am Post subject: Help with script pushing below address/byte shortage in loop Posted: Sat Nov 30, 2024 10:38 am Post subject: Help with script pushing below address/byte shortage in loop |
 |
|
Hello,
I've been stuck on editing a loop that links to integrity check.
Target is [esi+60] and [esi+70].
But since every address I cheat with is also accessed read by one of the below esi addresses I want to redirect them all just to be sure.
Specifically targetting all xmm's [esi]
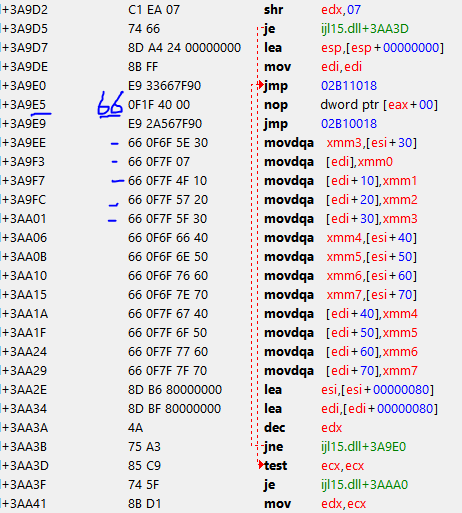
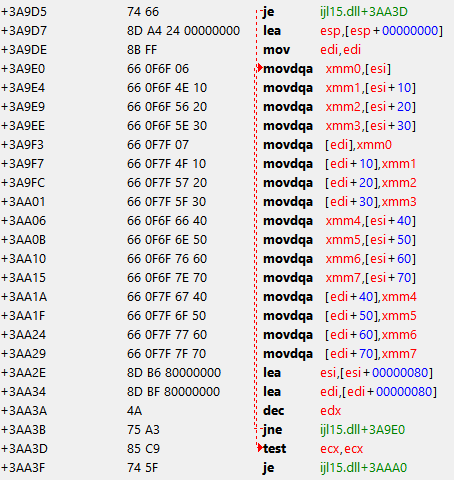
movdqa xmm0,[esi] <------- the one I get in trouble for the next one
movdqa xmm1,[esi+10] <----- address that gets affected by the script
movdqa xmm2,[esi+20]
movdqa xmm3,[esi+30] - ended the script here 4 the sake of length
movdqa xmm4,[esi+40]
movdqa xmm5,[esi+50]
movdqa xmm6,[esi+60] --->Checked by integrity check (always)
movdqa xmm7,[esi+70] --->Checked by integrity check
With the help/TUT of Dark Byte's video on youtube I made this script:
| Code: |
[ENABLE]
{$lua}
if addressOfCopy==nil then
addressOfCopy=copyMemory(getAddress(process), getModuleSize(process))
end
{$asm}
alloc(addressThatHoldsTheModuleBase,8)
alloc(addressThatHoldsTheModuleEnd,8)
alloc(addressThatHoldsTheCopyBase,8)
addressThatHoldsTheModuleBase:
dq $process
addressThatHoldsTheModuleBase:
dq $process+getModuleSize(process)
addressThatHoldsTheCopyBase:
dq addressOfCopy
//code from here to '[DISABLE]' will be used to enable the cheat
alloc(newmem3,2048)
label(returnhere3)
label(originalcode3)
label(exit3)
newmem3:
push rax
lea rax,[esi+20]
cmp rax,[addressThatHoldsTheModuleBase]
jb originalcode3
cmp rax,[addressThatHoldsTheModuleEnd]
ja originalcode3
sub rax,[addressThatHoldsTheModuleBase]
add rax,[addressThatHoldsTheCopyBase]
movdqa xmm2,[rax]
jmp exit3
originalcode3:
movdqa xmm2,[esi+20]
exit3:
pop rax
jmp returnhere3
"ijl15.dll"+3A9E9:
jmp newmem3
returnhere3:
alloc(newmem2,2048)
label(returnhere2)
label(originalcode2)
label(exit2)
newmem2:
push rax
lea rax,[esi+10]
cmp rax,[addressThatHoldsTheModuleBase]
jb originalcode2
cmp rax,[addressThatHoldsTheModuleEnd]
ja originalcode2
sub rax,[addressThatHoldsTheModuleBase]
add rax,[addressThatHoldsTheCopyBase]
movdqa xmm1,[rax]
jmp exit2
originalcode2:
movdqa xmm1,[esi+10]
exit2:
jmp returnhere2
"ijl15.dll"+3A9E4:
jmp newmem2
returnhere2:
alloc(newmem,2048)
label(returnhere)
label(originalcode)
label(exit)
newmem:
push rax
lea rax,[esi]
lea rax,[esi+10]
cmp rax,[addressThatHoldsTheModuleBase]
jb originalcode
cmp rax,[addressThatHoldsTheModuleEnd]
ja originalcode
sub rax,[addressThatHoldsTheModuleBase]
add rax,[addressThatHoldsTheCopyBase]
movdqa xmm0,[rax]
movdqa xmm1,[rax]
jmp exit
originalcode:
movdqa xmm0,[esi]
movdqa xmm1,[esi+10]
exit:
pop rax
jmp returnhere
"ijl15.dll"+3A9E0:
jmp newmem
nop 4
returnhere:
[DISABLE]
//code from here till the end of the code will be used to disable the cheat
dealloc(newmem3)
"ijl15.dll"+3A9E9:
db 66 0F 6F 56 20
//movdqa xmm2,[esi+20]
dealloc(newmem2)
"ijl15.dll"+3A9E4:
db 66 0F 6F 4E 10
//movdqa xmm1,[esi+10]
dealloc(newmem)
"ijl15.dll"+3A9E0:
db 66 0F 6F 06 66 0F 6F 4E 10
//movdqa xmm0,[esi]
//movdqa xmm1,[esi+10]
|
After I enable the script I see that the script needs 5 pairs of bytes
The 1st line originally only has 4 pairs of bytes.
In this case the script takes up another pair from the next(upcoming address) and ruins the following xmm1 address by 1 pair of bytes. (missing the beginning pair of opcode 66.
How can I solve this? how am I able to add space in between without disturbing the following addresses/opcodes?
I know that I can NOP extra bytes but what to do if you're short?
My second question is :
When I try to the opposite of 'movdqa xmm2,[esi+20]' in the script with xmm2 I get an error for example movdqa [edi+20],xmm2.
Is it correct to put it in like this without xmm2? (see below code newmem)
| Code: |
newmem:
push rax
lea rax,[esi+20] <------------- w/o the xmm2
cmp rax,[addressThatHoldsTheModuleBase]
jb originalcode
cmp rax,[addressThatHoldsTheModuleEnd]
ja originalcode
sub rax,[addressThatHoldsTheModuleBase]
add rax,[addressThatHoldsTheCopyBase]
movdqa [rax],xmm2
jmp exit
originalcode:
movdqa [edi+20],xmm2
exit:
pop rax
jmp returnhere
"ijl15.dll"+3A9FC:
jmp newmem
returnhere:
|
Any help is appreciated since i've been trying for a long time in many different ways and can't figure it out.
Thank in advance. (Dutch language is also welcome)
| Description: |
|
| Filesize: |
34.28 KB |
| Viewed: |
8382 Time(s) |
|
| Description: |
|
| Filesize: |
31.65 KB |
| Viewed: |
8382 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4724
|
 Posted: Sat Nov 30, 2024 12:52 pm Post subject: Posted: Sat Nov 30, 2024 12:52 pm Post subject: |
 |
|
You don't need to make a new code injection for every single instruction. Since the instructions are contiguous, you can extend a single code injection over the entire thing- i.e. inject at dll+3A9E0, `nop` a bunch more bytes after the `jmp` to your code (0x49 to be exact), and copy all the original code into your code injection. Make sure to restore all the bytes at the end too.
You shouldn't do that in this case, as there's a far better way to go about this.
The original code looks like part of a memcpy routine. Go to the start of it (might not be the start of the function) and inject code there. If the source points to an address within the exe, then change the source to point to your copy instead. Your code injection should be as simple as changing a single register.
If you can't read assembly that well, share more of the code around that area (especially above it) and maybe someone else can help.
Also, if you're not going to do an aobscan to find the injection point, use the "full injection" template instead.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
HamzInDaHouse
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 30 Nov 2024
Posts: 2
Location: Iraq
|
 Posted: Wed Jan 01, 2025 10:37 pm Post subject: Posted: Wed Jan 01, 2025 10:37 pm Post subject: |
 |
|
| ParkourPenguin wrote: | You don't need to make a new code injection for every single instruction. Since the instructions are contiguous, you can extend a single code injection over the entire thing- i.e. inject at dll+3A9E0, `nop` a bunch more bytes after the `jmp` to your code (0x49 to be exact), and copy all the original code into your code injection. Make sure to restore all the bytes at the end too.
You shouldn't do that in this case, as there's a far better way to go about this.
The original code looks like part of a memcpy routine. Go to the start of it (might not be the start of the function) and inject code there. If the source points to an address within the exe, then change the source to point to your copy instead. Your code injection should be as simple as changing a single register.
If you can't read assembly that well, share more of the code around that area (especially above it) and maybe someone else can help.
Also, if you're not going to do an aobscan to find the injection point, use the "full injection" template instead. |
Hello dear,
Thanks for your reply and your advice!
Is this how the script should look like for nopping the 49 and copy all the original code into the code injection?
| Code: |
[ENABLE]
{$lua}
if addressOfCopy==nil then
addressOfCopy=copyMemory(getAddress(process), getModuleSize(process))
end
{$asm}
alloc(addressThatHoldsTheModuleBase,8)
alloc(addressThatHoldsTheModuleEnd,8)
alloc(addressThatHoldsTheCopyBase,8)
addressThatHoldsTheModuleBase:
dq $process
addressThatHoldsTheModuleBase:
dq $process+getModuleSize(process)
addressThatHoldsTheCopyBase:
dq $addressOfCopy
alloc(newmem,2048)
label(returnhere)
label(originalcode)
label(exit)
newmem:
push rax
lea rax,[esi]
cmp rax,[addressThatHoldsTheModuleBase]
jb originalcode
cmp rax,[addressThatHoldsTheModuleEnd]
ja originalcode
sub rax,[addressThatHoldsTheModuleBase]
add rax,[addressThatHoldsTheCopyBase]
movdqa xmm0,[rax]
movdqa xmm1,[esi+10]
jmp exit
originalcode:
movdqa xmm0,[esi]
movdqa xmm1,[esi+10]
movdqa xmm2,[esi+20]
movdqa xmm3,[esi+30]
movdqa [edi],xmm0
movdqa [edi+10],xmm1
movdqa [edi+20],xmm2
movdqa [edi+30],xmm3
movdqa xmm4,[esi+40]
movdqa xmm5,[esi+50]
movdqa xmm6,[esi+60]
movdqa xmm7,[esi+70]
movdqa [edi+40],xmm4
movdqa [edi+50],xmm5
movdqa [edi+60],xmm6
movdqa [edi+70],xmm7
exit:
pop rax
jmp returnhere
"ijl15.dll"+3A9E0:
jmp newmem
nop 49
returnhere:
|
I also noticed much later that I forgot to put the $ sign in front of addressOfCopy after "dq" : | Code: | addressThatHoldsTheCopyBase:
dq addressOfCopy |
in the beginning of the script.
Does that dollar sign affect much?? Like will it work other than it should?
It was working until I reinstalled CE and I got the error in that line.
I will also definitely post/share more of the code around that area for a much simpler script and effective way!
Thanks again and excuse me for the late reply since I was away for a little while ^^.
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 152
Reputation: 152


