| View previous topic :: View next topic |
| Author |
Message |
MatrixModders
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 15 Mar 2023
Posts: 4
|
 Posted: Thu Mar 16, 2023 7:19 am Post subject: Use Opcode to search for code Posted: Thu Mar 16, 2023 7:19 am Post subject: Use Opcode to search for code |
 |
|
| I have an aob code that uses a dynamic address, however the opcode does not change even if it's a new address. Is there a way to search a browser PID using a series of opcodes and then replace them with the modified version or somehow get the aob from the opcodes? Furthermore, if this is possible; how can I use a template for opcode searches?[/b]
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4718
|
 Posted: Thu Mar 16, 2023 11:50 am Post subject: Posted: Thu Mar 16, 2023 11:50 am Post subject: |
 |
|
Are you talking about something like this:
| Code: | mov rax,00000460A38FC940
mov ecx,[rax] |
Where the address moved into rax changes when the game is restarted?
If so, manually replace the relevant bytes with wildcards (make sure the aobscan is still unique), use `readmem` to back up the original bytes at the injection point, and `reassemble` to execute the original code.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
MatrixModders
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 15 Mar 2023
Posts: 4
|
 Posted: Thu Mar 16, 2023 12:32 pm Post subject: Here Posted: Thu Mar 16, 2023 12:32 pm Post subject: Here |
 |
|
| ParkourPenguin wrote: | Are you talking about something like this:
| Code: | mov rax,00000460A38FC940
mov ecx,[rax] |
Where the address moved into rax changes when the game is restarted?
If so, manually replace the relevant bytes with wildcards (make sure the aobscan is still unique), use `readmem` to back up the original bytes at the injection point, and `reassemble` to execute the original code. |
I think I'm doing this reply back to you correctly but I have attached a Photo.
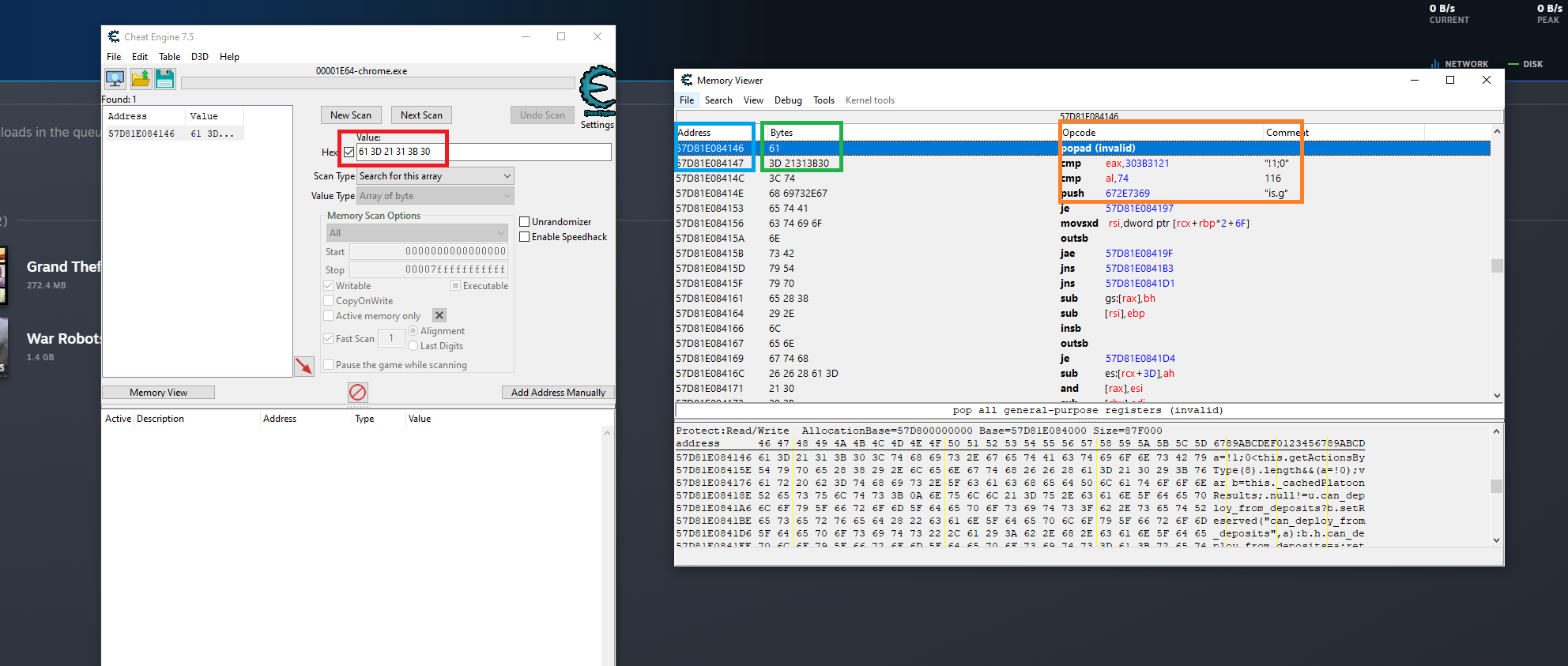
On the left part of the screen, you can see that I have an AOB that I scan for and it give's me a result of 1. Looking at the memory viewer, I already know that those addresses are dynamic and cannot be found towards a pointer address or anything. Furthermore, in the green and orange section are the bytes and opcode of the aob that I scanned. What I am asking is if there was a way to scan the opcode's only without knowing the address and scanning for the opcodes in that series or someway to scan for the comments you see but either way scan something for : cmp eax, 303B3121 etc...
| Description: |
|
| Filesize: |
278.69 KB |
| Viewed: |
2579 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4718
|
 Posted: Thu Mar 16, 2023 12:53 pm Post subject: Posted: Thu Mar 16, 2023 12:53 pm Post subject: |
 |
|
That doesn't look like code... it just looks like some ASCII string. Trying to interpret that as assembly code will only result in meaningless gibberish. The opcodes and comments you see at the top are worthless.
I don't know what your problem is. If you're trying to find the location of that string, just do an aobscan.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
MatrixModders
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 15 Mar 2023
Posts: 4
|
 Posted: Thu Mar 16, 2023 1:44 pm Post subject: again Posted: Thu Mar 16, 2023 1:44 pm Post subject: again |
 |
|
| I get what you are saying and yes, it's string text converted into aob, hence how I came up with the aob result. The problem is, the address changes every time the process is closed and reopened, whereas the opcodes in orange do not change no matter how many times the game is closed and reopened. The idea of a aobscan isn't so bad if I could find a static address to it, for which I don't. The string is part of the game which when I change 21 31 to 21 30; it enables part of the game that is hidden; similar to a true/false.
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4718
|
 Posted: Thu Mar 16, 2023 2:25 pm Post subject: Posted: Thu Mar 16, 2023 2:25 pm Post subject: |
 |
|
| MatrixModders wrote: | | The idea of a aobscan isn't so bad if I could find a static address to it, for which I don't. |
What? You don't need a static address for an aobscan. All an aobscan needs is an array of bytes to search for. If you had a static address, you wouldn't need to do an aobscan in the first place.
Those opcodes you see are just disassembled bytes. Scanning for opcodes is equivalent to scanning for bytes.
Maybe this AA script is what you're looking for?
| Code: | [ENABLE]
aobscan(my_important_text,61 3D 21 31 3B 30 3C 74 68 69 73 2E 67)
registersymbol(my_important_text)
[DISABLE]
unregistersymbol(my_important_text) |
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
|

 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152

