 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
DavidPS
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Oct 2016
Posts: 7
|
 Posted: Tue Oct 04, 2016 7:13 am Post subject: Android, how to ptrace? Posted: Tue Oct 04, 2016 7:13 am Post subject: Android, how to ptrace? |
 |
|
I managed to find process pointers with ceserver but now I want to find the way to read this values querying it with adb, but i don't know how to make the script to read the memory I read about ptrace but how implement pointers like "FileName.so+0x75" ?
Thx for your time.
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25796
Location: The netherlands
|
 Posted: Tue Oct 04, 2016 7:47 am Post subject: Posted: Tue Oct 04, 2016 7:47 am Post subject: |
 |
|
Look at /proc/(pid)/maps to find out where the module is loaded
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
DavidPS
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Oct 2016
Posts: 7
|
 Posted: Tue Oct 04, 2016 8:44 am Post subject: Posted: Tue Oct 04, 2016 8:44 am Post subject: |
 |
|
Then I must replace "FileName.so" for the starting adress of the module?
Also I read ptrace can be used only one time so, it means the app can check if you are debuging it right?... it make my plans unsafe... since i'm runing it as virtual machine any way to trace the module from host to avoid it?
Thx for your fast answer.
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25796
Location: The netherlands
|
 Posted: Tue Oct 04, 2016 9:09 am Post subject: Posted: Tue Oct 04, 2016 9:09 am Post subject: |
 |
|
you can also detach the ptrace. (ceserver attaches/detaches for debuggerless readmem)
and if you really want you can just compile your own linux kernel and shift the ptrace flag a bit and changr the API that reads it out
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
DavidPS
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Oct 2016
Posts: 7
|
 Posted: Tue Oct 04, 2016 10:03 am Post subject: Posted: Tue Oct 04, 2016 10:03 am Post subject: |
 |
|
I keep looking in google for a good example of ptrace to do it but i can't find any for:
attach to pid module -> read adress -> disattach
well to be honest I can't find any ptrace example working. ( maybe I need to install ptrace to my android emulator? )
I read the man docs so i know what options I can use but i don't know how implement it to an script.
So as last option i want to ask you if you can help me with a simple example.
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25796
Location: The netherlands
|
|
| Back to top |
|
 |
DavidPS
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Oct 2016
Posts: 7
|
 Posted: Tue Oct 04, 2016 1:36 pm Post subject: Posted: Tue Oct 04, 2016 1:36 pm Post subject: |
 |
|
this will do the job?
how to add the pointers to this?
| Code: | #include <stdio.h>
#include <string.h>
#include <sys/stat.h>
#include <sys/ptrace.h>
#include <sys/types.h>
#include <sys/wait.h>
#include <unistd.h>
#include <linux/user.h>
#include <fcntl.h>
#include <stdlib.h>
int main() {
pid_t pid = 1493; //PID example
uintptr_t lpAddress = 367017984; //Adress example
size_t size = 4; // read 4 bytes
void* buffer; // i'm not sure if init as void is ok...
int bread;
char* mem_file_name;
sprintf(mem_file_name, "/proc/%d/mem", pid);
int mem_fd = open(mem_file_name, O_RDONLY);
if (ptrace(PTRACE_ATTACH, pid, 0, 0) == 0)
{
int status;
pid = wait(&status);
lseek64(mem_fd, lpAddress, SEEK_SET);
bread = read(mem_fd, buffer, size);
if (bread == -1)
{
bread = 0;
printf("pread error for address %u ", lpAddress);
printf("\n");
}
printf("bread=%d size=%d\n", bread, size);
ptrace(PTRACE_DETACH, pid, 0, 0);
}
else
printf("ptrace attach failed (pid=%d). This system might not be properly rooted\n", pid);
}
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25796
Location: The netherlands
|
 Posted: Tue Oct 04, 2016 1:44 pm Post subject: Posted: Tue Oct 04, 2016 1:44 pm Post subject: |
 |
|
Add the baseaddress of xxx.so to the address, read the 4/8 byte value there. Add offset1 to that value, interpret it as an address, read the 4/8 byte value that address represents, etc...etc...etc...
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
DavidPS
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Oct 2016
Posts: 7
|
 Posted: Tue Oct 04, 2016 4:42 pm Post subject: Posted: Tue Oct 04, 2016 4:42 pm Post subject: |
 |
|
| Sorry if its a stupid question but i'm new with c compile for android. I need to use NDK and jni ?
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25796
Location: The netherlands
|
 Posted: Tue Oct 04, 2016 4:51 pm Post subject: Posted: Tue Oct 04, 2016 4:51 pm Post subject: |
 |
|
just the ndk
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
DavidPS
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Oct 2016
Posts: 7
|
 Posted: Tue Oct 04, 2016 10:08 pm Post subject: Posted: Tue Oct 04, 2016 10:08 pm Post subject: |
 |
|
I edited the script to be able to call it from comand line to this:
| Code: | #include <stdio.h>
#include <string.h>
#include <sys/stat.h>
#include <sys/ptrace.h>
#include <sys/types.h>
#include <sys/wait.h>
#include <unistd.h>
#include <fcntl.h>
int main(int argc, char* argv[]) {
if (argc > 1) {
pid_t pid = (pid_t)atoi(argv[0]); //PID example
uintptr_t lpAddress = (uintptr_t)atoi(argv[1]); //Adress example
size_t size = 4; // read 4 bytes
void* buffer = NULL; // i'm not sure if init as void is ok...
int bread;
char* mem_file_name;
sprintf(mem_file_name, "/proc/%d/mem", pid);
int mem_fd = open(mem_file_name, O_RDONLY);
if (ptrace(PTRACE_ATTACH, pid, 0, 0) == 0)
{
int status;
pid = wait(&status);
lseek64(mem_fd, lpAddress, SEEK_SET);
bread = read(mem_fd, buffer, size);
if (bread == -1)
{
bread = 0;
printf("pread error for address %u ", lpAddress);
printf("\n");
}
printf("bread=%d size=%d\n", bread, size);
ptrace(PTRACE_DETACH, pid, 0, 0);
}
else
printf("ptrace attach failed (pid=%d). This system might not be properly rooted\n", pid);
}
return 0;
} |
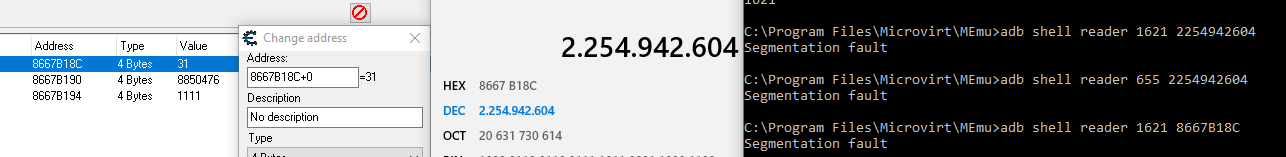
but after try it i have the following error: (Image try1.PNG)
I read it happen becouse i'm trying to read it without permission. Any clue about what i'm doing wrong?
Update----
I tryed to open the memory file after attatch but nothing changed 
Update2---
Tought o_RDONLY maybe wasn't enought so changed it to O_RDWR, but still having the same problem :/
| Description: |
|
| Filesize: |
20.28 KB |
| Viewed: |
18645 Time(s) |
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25796
Location: The netherlands
|
 Posted: Wed Oct 05, 2016 2:39 am Post subject: Posted: Wed Oct 05, 2016 2:39 am Post subject: |
 |
|
isn't argv[0] the processname of the program that's running?
buffer init as NULL isn't good. it must point to a valid memory address. (malloc can help with that, or use &buffer)
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
DavidPS
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Oct 2016
Posts: 7
|
 Posted: Wed Oct 05, 2016 7:32 am Post subject: Posted: Wed Oct 05, 2016 7:32 am Post subject: |
 |
|
Yay! Finally made it work, i'm not used to c so yes, argv[0] was wrong, also the type conversion and i was trying to edit a char*. I will post the code becouse i'm sure it can be usefull to someone, now i will try to do the pointer things! 
PS: Thankyou Dark Byte to be my lighthouse in this darkness area.
| Code: | #include <stdio.h>
#include <string.h>
#include <sys/stat.h>
#include <sys/ptrace.h>
#include <sys/types.h>
#include <sys/wait.h>
#include <unistd.h>
#include <fcntl.h>
int main(int argc, char* argv[]) {
if (argc > 2) {
pid_t pid = (pid_t)strtol(argv[1], NULL, 10);
uintptr_t lpAddress = (uintptr_t)strtoul(argv[2], NULL, 10);
size_t size = 4; // n bytes to read
char mem_file_name[20];
sprintf(mem_file_name, "/proc/%d/mem", pid);
uintptr_t buffer;
int bread;
if (ptrace(PTRACE_ATTACH, pid, 0, 0) == 0)
{
int status;
int mem_fd = open(mem_file_name, O_RDWR);
pid = wait(&status);
lseek64(mem_fd, lpAddress, SEEK_SET);
bread = read(mem_fd, &buffer, size);
if (bread == -1) printf("pread error for address %u ", lpAddress);
else printf("%u", buffer);
ptrace(PTRACE_DETACH, pid, 0, 0);
}
else printf("ptrace attach failed (pid=%d). This system might not be properly rooted", pid);
}
return 0;
} |
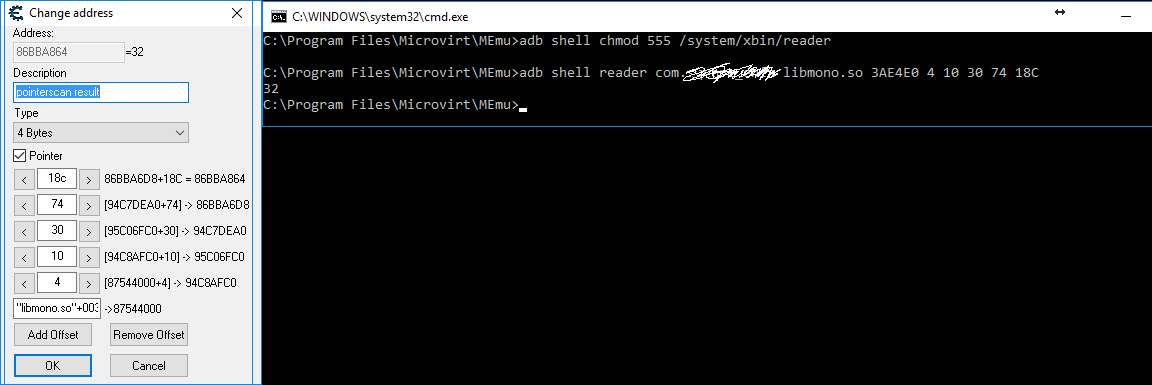
-----Udapte-------------
Here is the working code with an image explaining how to call it.
Hope it can help other ppl with questions like me and ofc all who read this topic can use it and improve it since i'm sure it can be improved
| Code: | #include <stdio.h>
#include <string.h>
#include <sys/stat.h>
#include <sys/ptrace.h>
#include <sys/types.h>
#include <sys/wait.h>
#include <unistd.h>
#include <fcntl.h>
int main(int argc, char* argv[]) {
if (argc > 2)
{
size_t size = 8;
// Get PID from apk name
char pid_query[200];
sprintf(pid_query, "ps | grep %s | awk '{ print $2 }'", argv[1]);
char Qpid[20];
FILE *pq = popen(pid_query, "r");
fscanf(pq, "%s", &Qpid);
pid_t pid = (pid_t)strtoul(Qpid, NULL, 10);
pclose(pq);
// Get Module Base Adress from Process Maps
char mem_file_name[20];
sprintf(mem_file_name, "/proc/%d/mem", pid);
char module_query[200];
sprintf(module_query, "cat /proc/%d/maps | grep %s | awk '{print $1}' | cut -f1 -d'-'", pid, argv[2]);
char Qaddr[20];
FILE *mq = popen(module_query, "r");
fscanf(mq, "%s", &Qaddr);
uintptr_t addr = (uintptr_t)strtoul(Qaddr, NULL, 16);
pclose(mq);
if (addr != 0)
{
ptrdiff_t offset = (ptrdiff_t)strtoul(argv[3], NULL, 16);
addr = (uintptr_t)(addr + offset);
if (ptrace(PTRACE_ATTACH, pid, 0, 0) == 0)
{
int status;
int mem_fd = open(mem_file_name, O_RDWR);
uintptr_t buffer;
int bread;
pid = wait(&status);
lseek64(mem_fd, addr, SEEK_SET);
bread = read(mem_fd, &buffer, size);
if (bread == -1) printf("pread error for address %u \n", addr);
else
{
// Loop over Pointer to find the end
int i;
for (i = 4; i < argc; i++)
{
offset = (ptrdiff_t)strtoul(argv[i], NULL, 16);
addr = (uintptr_t)(buffer + offset);
buffer = 0; //clean buffer
bread = 0; //clean bread
lseek64(mem_fd, addr, SEEK_SET);
bread = read(mem_fd, &buffer, size);
if (bread == -1)
{
printf("pread error for address %u \n", addr);
break;
}
}
printf("%u", buffer);
}
ptrace(PTRACE_DETACH, pid, 0, 0);
}
else printf("ptrace attach failed (pid=%d). This system might not be properly rooted \n", pid);
}
else printf("module not found on maps file (module=%s) \n", argv[2]);
}
return 0;
} |
| Description: |
|
| Filesize: |
21.02 KB |
| Viewed: |
18559 Time(s) |
|
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 470
Reputation: 470 Reputation: 470
Reputation: 470 Reputation: 470
Reputation: 470 Reputation: 470
Reputation: 470 Reputation: 470
Reputation: 470 Reputation: 470
Reputation: 470


