| View previous topic :: View next topic |
| Author |
Message |
Eraser
Grandmaster Cheater
 Reputation: 0 Reputation: 0
Joined: 23 Jul 2008
Posts: 504
Location: http://www.youtube.com/PCtrainers
|
 Posted: Sat Jun 29, 2013 4:08 am Post subject: AoB script is executed in the wrong address Posted: Sat Jun 29, 2013 4:08 am Post subject: AoB script is executed in the wrong address |
 |
|
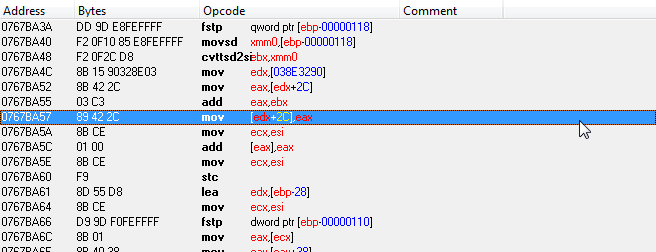
The code works nicely, but the problem is that sometimes there is more than one address that uses the same (89 42 2C) array of bytes which makes the code execute in the wrong address. My question is, how do I make it so it goes to the right address?
| Code: | [enable]
label(gold_address)
registersymbol(gold_address)
aobscan(gold,89 42 2C)
gold:
gold_address:
mov [edx+2C],186A0
mov ecx,esi
[disable]
gold_address:
mov [edx+2C],eax
mov ecx,esi
unregistersymbol(gold_address) |
Thanks!
| Description: |
|
| Filesize: |
11.56 KB |
| Viewed: |
4173 Time(s) |
|
|
|
| Back to top |
|
 |
TsTg
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 12 Dec 2012
Posts: 340
Location: Somewhere....
|
 Posted: Sat Jun 29, 2013 4:27 am Post subject: Posted: Sat Jun 29, 2013 4:27 am Post subject: |
 |
|
Use a longer AOB scan bytes, try this:
aobscan(gold,F2 0F 10 85 E8 FE FF FF F2 0F 2C D8 8B 15 90 32 8E 03 8B 42 2C 03 C3 89 42 2C 8B CE)
or use this one (if the address 038E3290 may get changed):
aobscan(gold,F2 0F 10 85 E8 FE FF FF F2 0F 2C D8 8B 15 ?? ?? ?? ?? 8B 42 2C 03 C3 89 42 2C 8B CE)
And To hack the mov [edx+2C],eax command, Start from gold+17, see the corrected script below:
| Code: | [enable]
label(gold_address)
registersymbol(gold_address)
aobscan(gold,F2 0F 10 85 E8 FE FF FF F2 0F 2C D8 8B 15 90 32 8E 03 8B 42 2C 03 C3 89 42 2C 8B CE)
gold+17:
gold_address:
mov [edx+2C],186A0
mov ecx,esi
[disable]
gold_address:
mov [edx+2C],eax
mov ecx,esi
unregistersymbol(gold_address) |
|
|
| Back to top |
|
 |
Eraser
Grandmaster Cheater
 Reputation: 0 Reputation: 0
Joined: 23 Jul 2008
Posts: 504
Location: http://www.youtube.com/PCtrainers
|
 Posted: Sat Jun 29, 2013 4:54 am Post subject: Posted: Sat Jun 29, 2013 4:54 am Post subject: |
 |
|
| Thanks! But what does the +17 do? Does not edit the first 17 bytes in the scan?
|
|
| Back to top |
|
 |
TsTg
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 12 Dec 2012
Posts: 340
Location: Somewhere....
|
 Posted: Sat Jun 29, 2013 4:59 am Post subject: Posted: Sat Jun 29, 2013 4:59 am Post subject: |
 |
|
nope, this AOB scan from the movsd xmm0,[ebp-00000118] command, which is BEFORE the target instruction: mov [edx+2C],eax, the +17 will tell CE to skip the first 23 bytes of the AOB chain (17 is hexadecimal of 23), so that it won't touch the wrong bytes.
0x767BA57 - 0x767BA40 = 0x17 HEX = 23 decimal
|
|
| Back to top |
|
 |
Eraser
Grandmaster Cheater
 Reputation: 0 Reputation: 0
Joined: 23 Jul 2008
Posts: 504
Location: http://www.youtube.com/PCtrainers
|
 Posted: Sat Jun 29, 2013 5:31 am Post subject: Posted: Sat Jun 29, 2013 5:31 am Post subject: |
 |
|
| Oh lol it was in hex, thanks a lot for explaining
|
|
| Back to top |
|
 |
|

 Reputation: 0
Reputation: 0 Reputation: 5
Reputation: 5 Reputation: 0
Reputation: 0 Reputation: 5
Reputation: 5 Reputation: 0
Reputation: 0

