 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
Rubyelf
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2013
Posts: 29
|
 Posted: Mon May 06, 2024 12:15 am Post subject: Help with fixing this script Posted: Mon May 06, 2024 12:15 am Post subject: Help with fixing this script |
 |
|
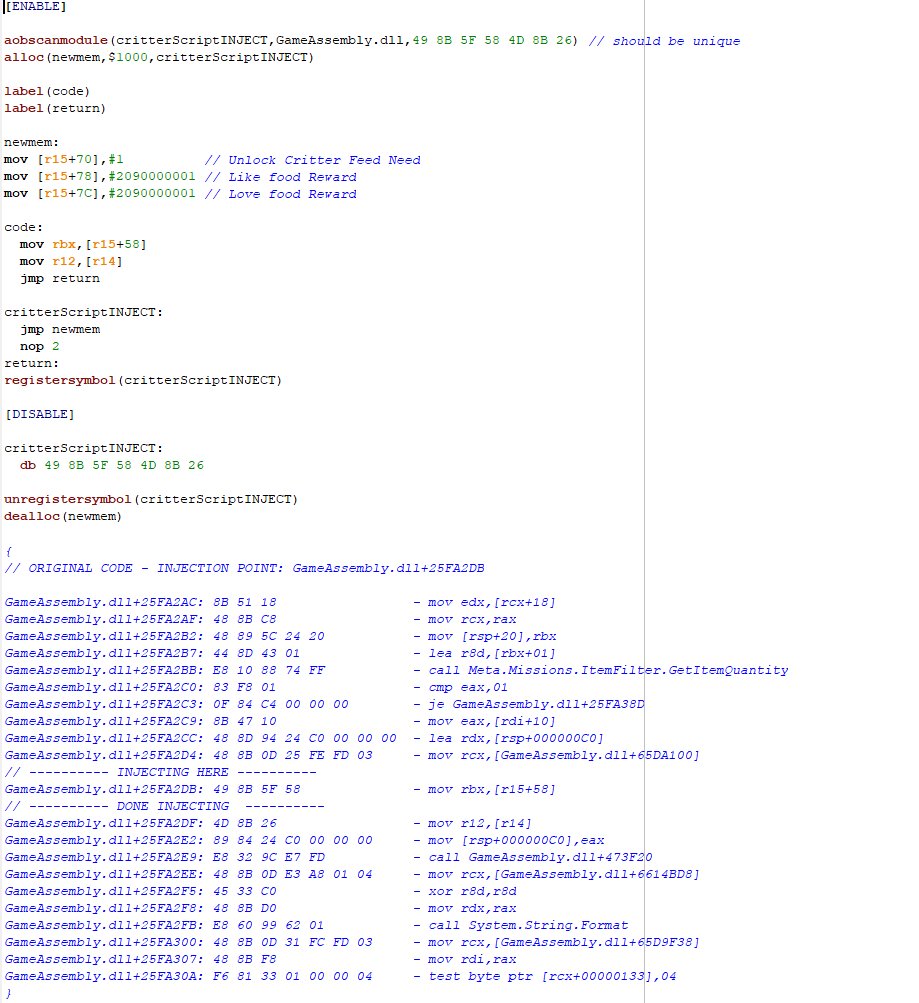
I am attempting to fix a script, which I've attached a screenshot of.
Obviously the AOB is not working in my favour, and I know that the opcode "Meta.Missions.ItemFilter.GetItemQuantity" still exists, but I have no idea how to search for it (using mono + ctrl G doesn't find it as an address, and I did try searching assembly code....but even being left on over night for 10 hours it didn't finish so it was a bit slow, and I'm not sure how to speed that process up).
I am not sure which part of the code I should try and use wildcards for as I am still very new to learning how to do this.
All I am 100% certain about is that the object in question does use "2090000001" as it's "item type".
| Description: |
|
| Filesize: |
62.75 KB |
| Viewed: |
6582 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4711
|
 Posted: Mon May 06, 2024 11:20 am Post subject: Posted: Mon May 06, 2024 11:20 am Post subject: |
 |
|
| Rubyelf wrote: | | Obviously the AOB is not working in my favour |
Why "obviously"? If you let CE generate the aobscan script from a template, it should be fine.
In the main CE window, change the value type to Array of Bytes and copy/paste the aob pattern in the search field. Change the region you're scanning from "All" to GameAssembly.dll. Also right click in the Writable / Executable / Copy on Write region and select "Preset: scan all memory".
Then scan for the aob. If only one result comes up, you're fine. If more than one result comes up, you need to extend the pattern until you find a place where they differ.
| Rubyelf wrote: | | I am not sure which part of the code I should try and use wildcards for as I am still very new to learning how to do this. |
I don't see anything you should replace with wildcards.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Rubyelf
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2013
Posts: 29
|
 Posted: Mon May 06, 2024 12:08 pm Post subject: Posted: Mon May 06, 2024 12:08 pm Post subject: |
 |
|
| ParkourPenguin wrote: | | Rubyelf wrote: | | Obviously the AOB is not working in my favour |
Why "obviously"? If you let CE generate the aobscan script from a template, it should be fine.
In the main CE window, change the value type to Array of Bytes and copy/paste the aob pattern in the search field. Change the region you're scanning from "All" to GameAssembly.dll. Also right click in the Writable / Executable / Copy on Write region and select "Preset: scan all memory".
Then scan for the aob. If only one result comes up, you're fine. If more than one result comes up, you need to extend the pattern until you find a place where they differ.
| Rubyelf wrote: | | I am not sure which part of the code I should try and use wildcards for as I am still very new to learning how to do this. |
I don't see anything you should replace with wildcards. |
That's the problem I cannot find the AOB, it no longer exists, which is what I meant by it's not working, sorry it was 1am when I posted and I was very tired.
I've been able to fix/find most other scripts on this broken table, but this one has eluded me. I tried your suggestion and get 0 results.
I can find 12 entries matching "49 8B 5F 58" part of the AOB, but none of them seem to line up with what the old code was.
May "Meta.Missions.ItemFilter.GetItemQuantity" has been removed or changed because I cannot find that either an AOB scan
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4711
|
 Posted: Mon May 06, 2024 12:44 pm Post subject: Posted: Mon May 06, 2024 12:44 pm Post subject: |
 |
|
Oh, that was a script generated from an older version of the game. I see now.
A lot of stuff could've changed. Offsets, registers, instruction sizes (e.g. REX prefixes), the order of instructions, etc. There isn't an easy guaranteed way to find the new injection point.
That first call looks like a decent place to start from. Try this pattern:
E8 ?? ?? ?? ?? 83 F8 01 0F 84 ?? ?? 00 00 8B
That `je` is annoying because the offset isn't that far away. It could be using a `je rel8` opcode instead of `je rel32` opcode.
Maybe the couple calls below the injection point could be good too.
E8 ?? ?? ?? ?? 48 8B 0D ?? ?? ?? ?? 45 33 C0 48 8B D0 E8
If that fails, you could try methodically searching for that call to Meta.Missions.ItemFilter.GetItemQuantity. An easy way is to run "Memory Viewer -> Tools -> Dissect code" on that dll. That might take a while (roughly an hour or two) depending on how big the dll is. When you're done, you can select File -> Save in the dissect code window so you don't have to do that again next time.
After that completes, just go to Meta.Missions.ItemFilter.GetItemQuantity in the disassembler and see what calls that address. You can use Lua to help:
| Code: | local addr = assert(getAddressSafe'Tutorial-x86_64.exe+FC10', 'Invalid address')
local t = {}
for addr,reftype in pairs(getDissectCode().getReferences(addr)) do
if reftype == jtCall then
t[#t+1] = addr
end
end
table.sort(t, function(lhs, rhs) return lhs < rhs end)
for _,v in ipairs(t) do
print(getNameFromAddress(v))
end |
If even that's too slow, you could make a custom type that searches for `call rel32` opcodes to a certain address.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Rubyelf
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2013
Posts: 29
|
 Posted: Mon May 06, 2024 1:02 pm Post subject: Posted: Mon May 06, 2024 1:02 pm Post subject: |
 |
|
| ParkourPenguin wrote: | Oh, that was a script generated from an older version of the game. I see now.
A lot of stuff could've changed. Offsets, registers, instruction sizes (e.g. REX prefixes), the order of instructions, etc. There isn't an easy guaranteed way to find the new injection point.
That first call looks like a decent place to start from. Try this pattern:
E8 ?? ?? ?? ?? 83 F8 01 0F 84 ?? ?? 00 00 8B
That `je` is annoying because the offset isn't that far away. It could be using a `je rel8` opcode instead of `je rel32` opcode.
Maybe the couple calls below the injection point could be good too.
E8 ?? ?? ?? ?? 48 8B 0D ?? ?? ?? ?? 45 33 C0 48 8B D0 E8
If that fails, you could try methodically searching for that call to Meta.Missions.ItemFilter.GetItemQuantity. An easy way is to run "Memory Viewer -> Tools -> Dissect code" on that dll. That might take a while (roughly an hour or two) depending on how big the dll is. When you're done, you can select File -> Save in the dissect code window so you don't have to do that again next time.
After that completes, just go to Meta.Missions.ItemFilter.GetItemQuantity in the disassembler and see what calls that address. You can use Lua to help:
| Code: | local addr = assert(getAddressSafe'Tutorial-x86_64.exe+FC10', 'Invalid address')
local t = {}
for addr,reftype in pairs(getDissectCode().getReferences(addr)) do
if reftype == jtCall then
t[#t+1] = addr
end
end
table.sort(t, function(lhs, rhs) return lhs < rhs end)
for _,v in ipairs(t) do
print(getNameFromAddress(v))
end |
If even that's too slow, you could make a custom type that searches for `call rel32` opcodes to a certain address. |
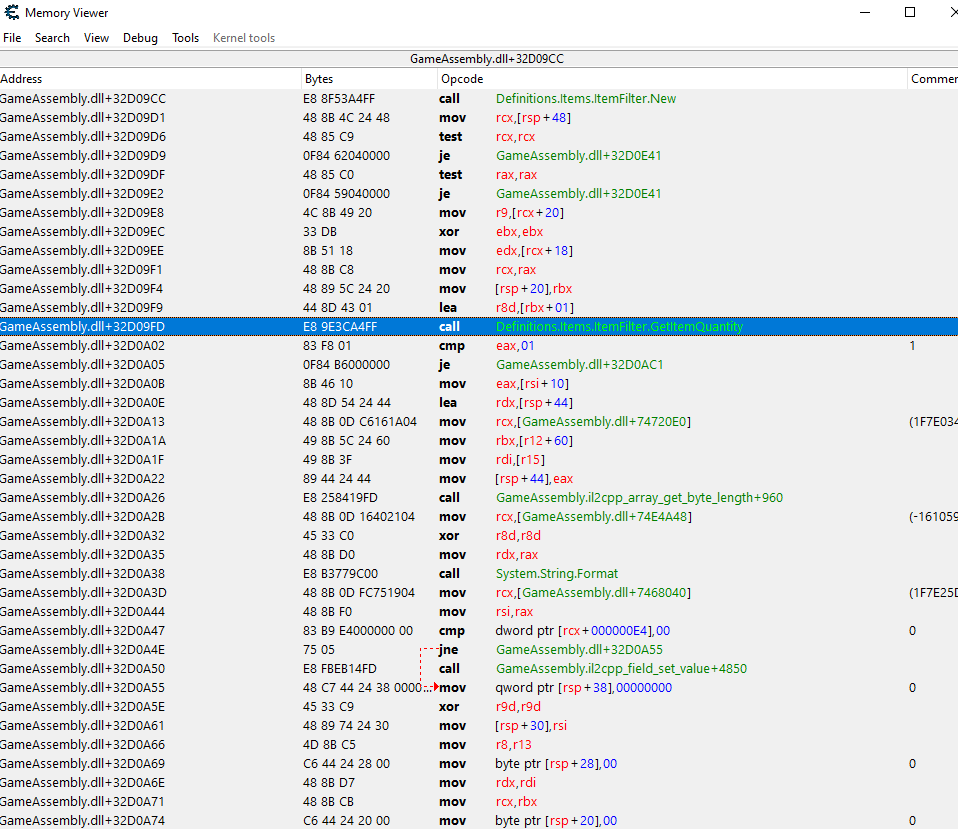
My first search actually yielded something very close:
- call Definitions.Items.ItemFilter.GetItemQuantity
So maybe they changed Meta to Definitions.Items?
The second one resulted in about 50+ results, which I am slowly going through right now though to check, but that first one was the closest to similar.
I posted a pic
EDIT: It looks like that might have been it, when I checked what addressed this function and fed 2 critters it actually ticked off each time as being addressed.
Problem is, I'm not sure how to go about updating the new code part
| Code: | newmem:
mov [r15+70],#1 // Unlock Critter Feed Need
mov [r15+78],#2090000001 // Like food Reward
mov [r15+7C],#2090000001 // Love food Reward
code:
mov rbx,[r15+58]
mov r12,[r14]
jmp return |
As it crashed my game with my attempts...which I assume I did something wrong.
| Description: |
|
| Filesize: |
71.61 KB |
| Viewed: |
6483 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4711
|
 Posted: Mon May 06, 2024 1:23 pm Post subject: Posted: Mon May 06, 2024 1:23 pm Post subject: |
 |
|
Yes, that looks as close to it as you can get. The calls, static addresses, memory accesses, etc. are all in the same place. It's just the registers and offsets that have changed.
The instruction you want to inject at is at dll+32D0A1A - `mov rbx,[r12+60]`. Open a new AA window and make a new AOB injection template at that address.
You'll need to change the injected code too: obviously change r15 to r12, but as for the offsets the injected code uses, I'm not certain. You'll need to dissect data and figure it out. Since the new offset in the original code is 8 bytes after the old offset, perhaps it's the same for those other offsets: I'd check the values at the offsets 78, 80, and 84 first.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Rubyelf
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2013
Posts: 29
|
 Posted: Mon May 06, 2024 1:28 pm Post subject: Posted: Mon May 06, 2024 1:28 pm Post subject: |
 |
|
| ParkourPenguin wrote: | Yes, that looks as close to it as you can get. The calls, static addresses, memory accesses, etc. are all in the same place. It's just the registers and offsets that have changed.
The instruction you want to inject at is at dll+32D0A1A - `mov rbx,[r12+60]`. Open a new AA window and make a new AOB injection template at that address.
You'll need to change the injected code too: obviously change r15 to r12, but as for the offsets the injected code uses, I'm not certain. You'll need to dissect data and figure it out. Since the new offset in the original code is 8 bytes after the old offset, perhaps it's the same for those other offsets: I'd check the values at the offsets 78, 80, and 84 first. |
I'm guessing you mean change
| Code: | newmem:
mov [r15+70],#1 // Unlock Critter Feed Need
mov [r15+78],#2090000001 // Like food Reward
mov [r15+7C],#2090000001 // Love food Reward |
To
| Code: |
newmem:
mov [r12+78],#1 // Unlock Critter Feed Need
mov [r12+80],#2090000001 // Like food Reward
mov [r12+84],#2090000001 // Love food Reward |
? Sorry I am still very new and trying to learn, and I appreciate all the help so far you've been amazing in getting me this close!
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4711
|
 Posted: Mon May 06, 2024 1:44 pm Post subject: Posted: Mon May 06, 2024 1:44 pm Post subject: |
 |
|
Yes, but I'd try dissect data first.
Find out what addresses the instruction `mov rbx,[r12+60]` accesses (right click it in the disassembler), let the game run for a little while and do whatever you need to do to trigger that code to run, select everything that comes up, and right click -> Open dissect data with selected addresses
Then just visually inspect what's around offset 70 through 90. Maybe you'll see something that sticks out, or maybe you won't. Changing random values can also be effective- just make sure you have a backup of your save somewhere.
Also, make sure you generate a new AOB injection template. Don't reuse the old script. The original code obviously changed, and you'll want to keep a copy of the instructions around the new injection point.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Rubyelf
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2013
Posts: 29
|
 Posted: Mon May 06, 2024 1:59 pm Post subject: Posted: Mon May 06, 2024 1:59 pm Post subject: |
 |
|
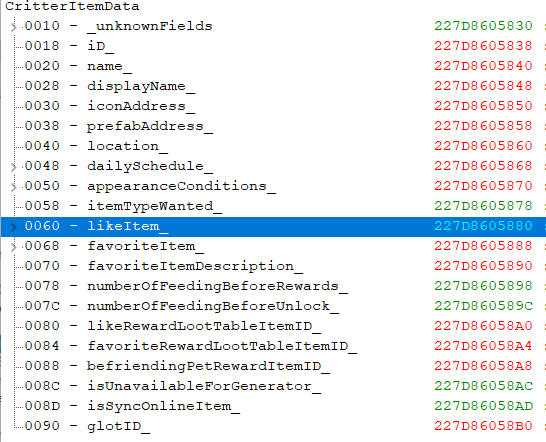
| ParkourPenguin wrote: | Yes, but I'd try dissect data first.
Find out what addresses the instruction `mov rbx,[r12+60]` accesses (right click it in the disassembler), let the game run for a little while and do whatever you need to do to trigger that code to run, select everything that comes up, and right click -> Open dissect data with selected addresses
Then just visually inspect what's around offset 70 through 90. Maybe you'll see something that sticks out, or maybe you won't. Changing random values can also be effective- just make sure you have a backup of your save somewhere.
Also, make sure you generate a new AOB injection template. Don't reuse the old script. The original code obviously changed, and you'll want to keep a copy of the instructions around the new injection point. |
This looks promising! (But I didn't get this part from watching the mov rbx,[r12+60] part....it came from watching the gameassembly part, as nothing was showing up watching the first one.
| Description: |
|
| Filesize: |
26.94 KB |
| Viewed: |
6439 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4711
|
 Posted: Mon May 06, 2024 2:16 pm Post subject: Posted: Mon May 06, 2024 2:16 pm Post subject: |
 |
|
Good, there's debug/reflection info available for fields too.
It's probably 78, 80, and 84. Offset 7C looks interesting too, but do whatever you want.
| Rubyelf wrote: | | it came from watching the gameassembly part |
What instruction did you look at?
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Rubyelf
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2013
Posts: 29
|
 Posted: Mon May 06, 2024 2:35 pm Post subject: Posted: Mon May 06, 2024 2:35 pm Post subject: |
 |
|
| ParkourPenguin wrote: | Good, there's debug/reflection info available for fields too.
It's probably 78, 80, and 84. Offset 7C looks interesting too, but do whatever you want.
| Rubyelf wrote: | | it came from watching the gameassembly part |
What instruction did you look at? |
GameAssembly.dll+32D0A1A
That one - as trying to watch GameAssembly.dll+32D0A1A - mov rbx,[r12+60]
yielded nothing at all...
Unfortunately changing those codes didn't yeild anything either as the rewards did not give me the one I'm telling it to (it's giving me the usual random ones).
Last edited by Rubyelf on Mon May 06, 2024 2:42 pm; edited 1 time in total |
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4711
|
 Posted: Mon May 06, 2024 2:40 pm Post subject: Posted: Mon May 06, 2024 2:40 pm Post subject: |
 |
|
You probably have that the other way around. `call rel32` instructions can't trigger "Find out what addresses this instruction accesses".
Anyway, post the script you're using.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Rubyelf
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2013
Posts: 29
|
 Posted: Mon May 06, 2024 2:43 pm Post subject: Posted: Mon May 06, 2024 2:43 pm Post subject: |
 |
|
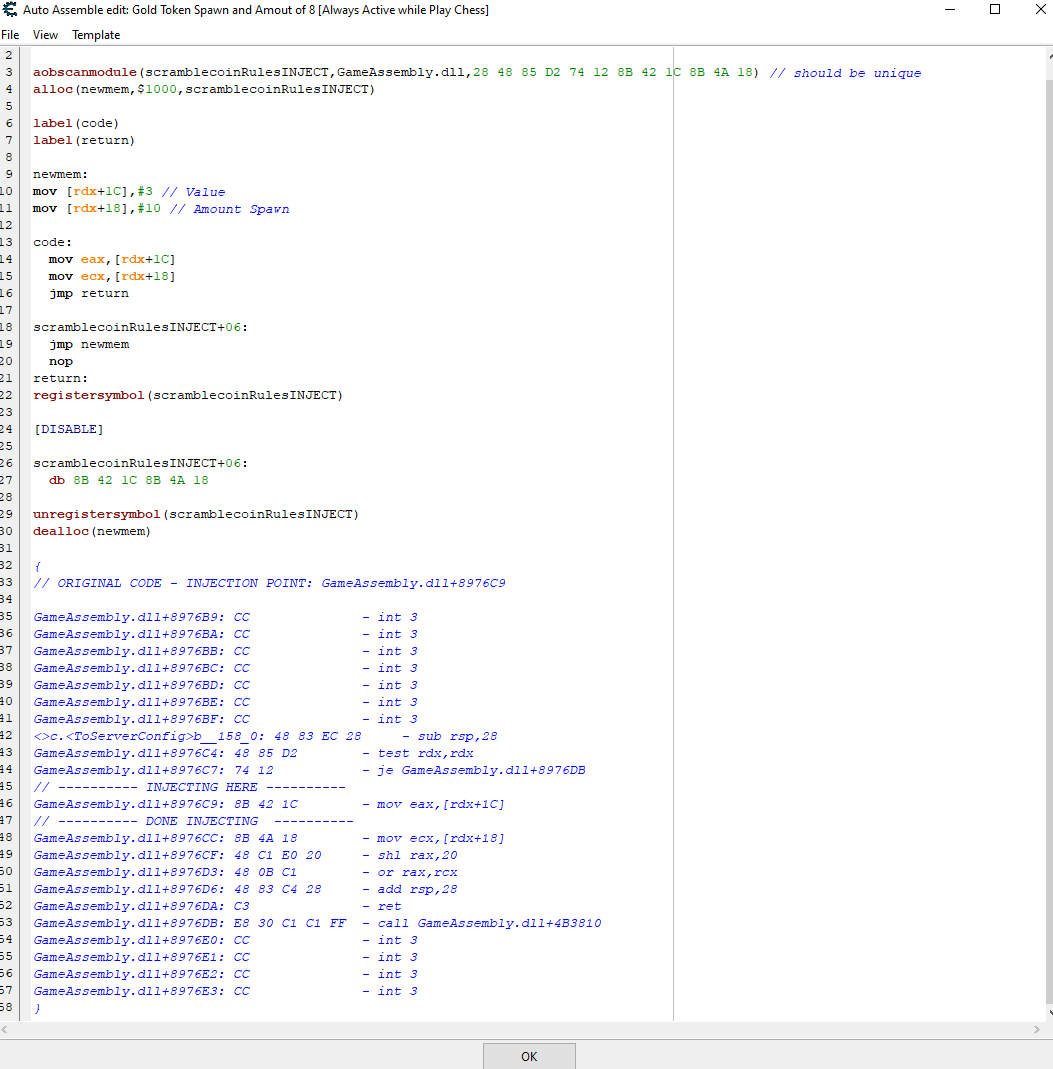
| ParkourPenguin wrote: | You probably have that the other way around. `call rel32` instructions can't trigger "Find out what addresses this instruction accesses".
Anyway, post the script you're using. |
Here, but I've got it all wrong in what I was searching and what showed changes and got me the other codes...
| Code: | [ENABLE]
aobscanmodule(critterScriptINJECT,GameAssembly.dll,49 8B 5C 24 60 49) // should be unique
alloc(newmem,$1000,critterScriptINJECT)
label(code)
label(return)
newmem:
mov [r12+78],#1 // Unlock Critter Feed Need
mov [r12+80],#2090000001 // Like food Reward
mov [r12+84],#2090000001 // Love food Reward
code:
mov rbx,[r12+60]
jmp return
critterScriptINJECT:
jmp newmem
nop 2
return:
registersymbol(critterScriptINJECT)
[DISABLE]
critterScriptINJECT:
db 49 8B 5C 24 60
unregistersymbol(critterScriptINJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: GameAssembly.dll+32D0A1A
GameAssembly.dll+32D09EE: 8B 51 18 - mov edx,[rcx+18]
GameAssembly.dll+32D09F1: 48 8B C8 - mov rcx,rax
GameAssembly.dll+32D09F4: 48 89 5C 24 20 - mov [rsp+20],rbx
GameAssembly.dll+32D09F9: 44 8D 43 01 - lea r8d,[rbx+01]
GameAssembly.dll+32D09FD: E8 9E 3C A4 FF - call Definitions.Items.ItemFilter.GetItemQuantity
GameAssembly.dll+32D0A02: 83 F8 01 - cmp eax,01
GameAssembly.dll+32D0A05: 0F 84 B6 00 00 00 - je GameAssembly.dll+32D0AC1
GameAssembly.dll+32D0A0B: 8B 46 10 - mov eax,[rsi+10]
GameAssembly.dll+32D0A0E: 48 8D 54 24 44 - lea rdx,[rsp+44]
GameAssembly.dll+32D0A13: 48 8B 0D C6 16 1A 04 - mov rcx,[GameAssembly.dll+74720E0]
// ---------- INJECTING HERE ----------
GameAssembly.dll+32D0A1A: 49 8B 5C 24 60 - mov rbx,[r12+60]
// ---------- DONE INJECTING ----------
GameAssembly.dll+32D0A1F: 49 8B 3F - mov rdi,[r15]
GameAssembly.dll+32D0A22: 89 44 24 44 - mov [rsp+44],eax
GameAssembly.dll+32D0A26: E8 25 84 19 FD - call GameAssembly.il2cpp_array_get_byte_length+960
GameAssembly.dll+32D0A2B: 48 8B 0D 16 40 21 04 - mov rcx,[GameAssembly.dll+74E4A48]
GameAssembly.dll+32D0A32: 45 33 C0 - xor r8d,r8d
GameAssembly.dll+32D0A35: 48 8B D0 - mov rdx,rax
GameAssembly.dll+32D0A38: E8 B3 77 9C 00 - call System.String.Format
GameAssembly.dll+32D0A3D: 48 8B 0D FC 75 19 04 - mov rcx,[GameAssembly.dll+7468040]
GameAssembly.dll+32D0A44: 48 8B F0 - mov rsi,rax
GameAssembly.dll+32D0A47: 83 B9 E4 00 00 00 00 - cmp dword ptr [rcx+000000E4],00
} |
Argh this time it worked from that the one you told me to check, I honestly have no idea wth, maybe I clicked on something accidentally and didn't realise....
Still trying to fix the table though as it doesnt give me the desired reward (and I know that hasnt' changed as I've used it for OTHER tasks to give the same reward).
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4711
|
 Posted: Mon May 06, 2024 3:00 pm Post subject: Posted: Mon May 06, 2024 3:00 pm Post subject: |
 |
|
| Rubyelf wrote: | | ParkourPenguin wrote: | | What instruction did you look at? |
GameAssembly.dll+32D0A1A
That one - as trying to watch GameAssembly.dll+32D0A1A - mov rbx,[r12+60]
yielded nothing at all... |
That's the same instruction. Note that the instruction has to be executed in order for CE to note which addresses it accesses. If you don't do a certain action in-game to cause the game to execute that instruction, it won't get executed, and nothing will show up in the window.
When is that injection point run? Is it when you open a menu, or when a critter spawns? If it's not run before you're suppose to get that item, then the values won't be written, and it won't work.
Close the game and CE, start the game, attach CE to the game, enable the script, and then start playing and see if it works.
If it does, you might not have had the script active, or you had something else messing with things.
If it doesn't, then maybe the injection point isn't running when you think it does, or it's the wrong injection point entirely.
Instead of following that old script, you could try making your own. Look at what instructions access an address at offset 78 instead. e.g. in crit.png, 227D8605898
Pick an instruction that's run often enough and inject that code there. (the registers might change)
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Rubyelf
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2013
Posts: 29
|
 Posted: Mon May 06, 2024 3:33 pm Post subject: Posted: Mon May 06, 2024 3:33 pm Post subject: |
 |
|
I fixed it! Thank you so much for all the help!
I messed up somewhere along the way when swapping it over and got it fixed!
Now I need to figure out this one.
In the past I could search "<>c.<ToServerConfig>b__158_0" with mono, but it no longer exists, and the ones that have similar names don't appear to look anything like it anymore.
| Description: |
|
| Filesize: |
67.49 KB |
| Viewed: |
6358 Time(s) |
|
Last edited by Rubyelf on Mon May 06, 2024 5:41 pm; edited 1 time in total |
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152




