| View previous topic :: View next topic |
| Author |
Message |
CerberusForHumanity
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 06 Mar 2019
Posts: 12
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 153 Reputation: 153
Joined: 06 Jul 2014
Posts: 4735
|
 Posted: Thu Apr 23, 2020 11:17 pm Post subject: Posted: Thu Apr 23, 2020 11:17 pm Post subject: |
 |
|
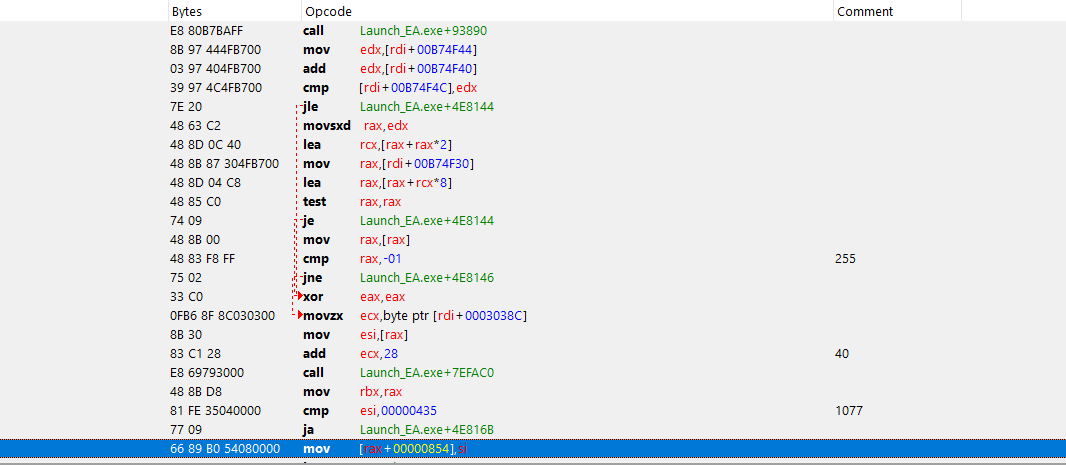
Every path going to exe+4e8144 causes a segfault. Relying on exceptions as an ordinary branching mechanism seems like a stupid thing to do intentionally, so it's probably just crashing the game on purpose.
Check what the values at rdi+b74f4c and rdi+b74f44 are.
The value in edx is being used as an offset from the value in rdi+b74f30. There are a couple places it could segfault if set improperly with respect to rdi+b74f40. Maybe rdi+b74f44 is a negative number that results in a reasonable offset after the add? Or perhaps that value at rdi+b74f30 is important too? The address that results from mov rax,[rax] is read to get the value written to esi and, if the function exe+7efac0 conforms to any standard calling convention, subsequently the value stored at rax+854.
Debug it to look at values in registers and in memory, and use your head to figure out the meaning of the different values. Maybe look at the called function too, especially if esi isn't preserved across it.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
CerberusForHumanity
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 06 Mar 2019
Posts: 12
|
 Posted: Fri Apr 24, 2020 12:42 am Post subject: Posted: Fri Apr 24, 2020 12:42 am Post subject: |
 |
|
| ParkourPenguin wrote: | Every path going to exe+4e8144 causes a segfault. Relying on exceptions as an ordinary branching mechanism seems like a stupid thing to do intentionally, so it's probably just crashing the game on purpose.
Check what the values at rdi+b74f4c and rdi+b74f44 are.
The value in edx is being used as an offset from the value in rdi+b74f30. There are a couple places it could segfault if set improperly with respect to rdi+b74f40. Maybe rdi+b74f44 is a negative number that results in a reasonable offset after the add? Or perhaps that value at rdi+b74f30 is important too? The address that results from mov rax,[rax] is read to get the value written to esi and, if the function exe+7efac0 conforms to any standard calling convention, subsequently the value stored at rax+854.
Debug it to look at values in registers and in memory, and use your head to figure out the meaning of the different values. Maybe look at the called function too, especially if esi isn't preserved across it. |
so i tried putting a script in multiple locations but it seems anything before the selected opcode causes a crash regardless of the value i put. i must be messing up i just did not think making a script where it first gets its value would cause crashes. i can make a script after the encryption but not before it until i can figure out the issue.
|
|
| Back to top |
|
 |
CerberusForHumanity
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 06 Mar 2019
Posts: 12
|
 Posted: Thu Apr 30, 2020 8:23 pm Post subject: Posted: Thu Apr 30, 2020 8:23 pm Post subject: |
 |
|
so from more digging i found at the compare the value of the cap is 30 and when i do what writes to it instead of seeing 1E (hex for 30) i see no values except zeros at edi like in these images. i also know edi got its value at the push. at the push it shows no value except zeros when using a breakpoint. How do i see the 30/1E if breakpoint and the what writes menu doesnt show it either? i know it is 30 because when i do a what addresses this instruction accesses it shows a address with a byte value of 30. it makes sense since the unit cap is 30. thank you for your time and anyone that helps and has helped.
| Description: |
|
| Filesize: |
197 KB |
| Viewed: |
2062 Time(s) |

|
| Description: |
|
| Filesize: |
333.24 KB |
| Viewed: |
2062 Time(s) |

|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 153 Reputation: 153
Joined: 06 Jul 2014
Posts: 4735
|
 Posted: Thu Apr 30, 2020 10:05 pm Post subject: Posted: Thu Apr 30, 2020 10:05 pm Post subject: |
 |
|
There's an xor edi,edi just before that write (mov [rcx+3cc],edi), so yes, it's being set to 0.
(xor edi,edi sets edi to 0 always)
The inc instruction probably increments the value until it reaches 30 or something.
| CerberusForHumanity wrote: | | i also know edi got its value at the push |
What push are you talking about? The one at exe+6B1195 (label "tty")? That's just backing up the register, as per standard calling conventions. push instructions don't even write to registers.
Perhaps you should start smaller and learn what instructions do.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
CerberusForHumanity
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 06 Mar 2019
Posts: 12
|
 Posted: Thu Apr 30, 2020 10:14 pm Post subject: Posted: Thu Apr 30, 2020 10:14 pm Post subject: |
 |
|
| ParkourPenguin wrote: | There's an xor edi,edi just before that write (mov [rcx+3cc],edi), so yes, it's being set to 0.
(xor edi,edi sets edi to 0 always)
The inc instruction probably increments the value until it reaches 30 or something.
| CerberusForHumanity wrote: | | i also know edi got its value at the push |
What push are you talking about? The one at exe+6B1195 (label "tty")? That's just backing up the register, as per standard calling conventions. push instructions don't even write to registers.
Perhaps you should start smaller and learn what instructions do. |
my bad i had thought it was pushing the value that is in edi. i am half awake while trying to figure things out so i apologize for the misunderstanding
|
|
| Back to top |
|
 |
|

 Reputation: 153
Reputation: 153 Reputation: 153
Reputation: 153