| View previous topic :: View next topic |
| Author |
Message |
Erik9631
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 24 Aug 2014
Posts: 10
|
 Posted: Sat Feb 29, 2020 7:47 pm Post subject: Calculating offset to base pointer Posted: Sat Feb 29, 2020 7:47 pm Post subject: Calculating offset to base pointer |
 |
|
Hello.
I am a bit new to reverse engineering and I need some help figuring out how to calculate the static offset to the base pointer (I believe the offset should be the difference between the main application and the pointer address), so once the application is restarted, I always get to the address of the pointer. (But please correct me if I am wrong)
I created a simple application with the following code:
| Code: |
int main()
{
HANDLE moduleHandle = GetModuleHandle("Delete.exe");
cout << moduleHandle << endl;
int* hackableValue = new int[1];
*hackableValue = 5;
system("PAUSE");
while (1)
{
if (GetAsyncKeyState(VK_UP) & ((unsigned short)32768))
{
*hackableValue += 2;
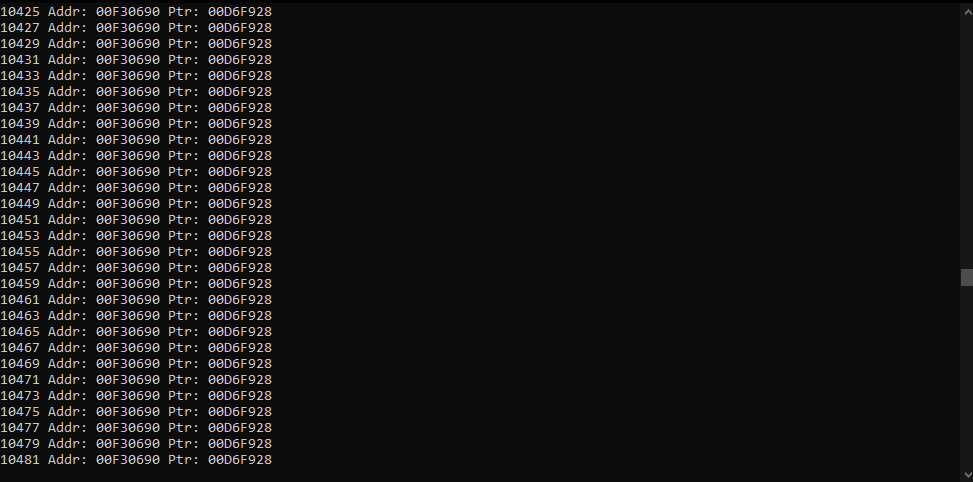
cout << *hackableValue << " Addr: " << hackableValue << " Ptr: "<< &hackableValue <<endl;
}
}
}
|
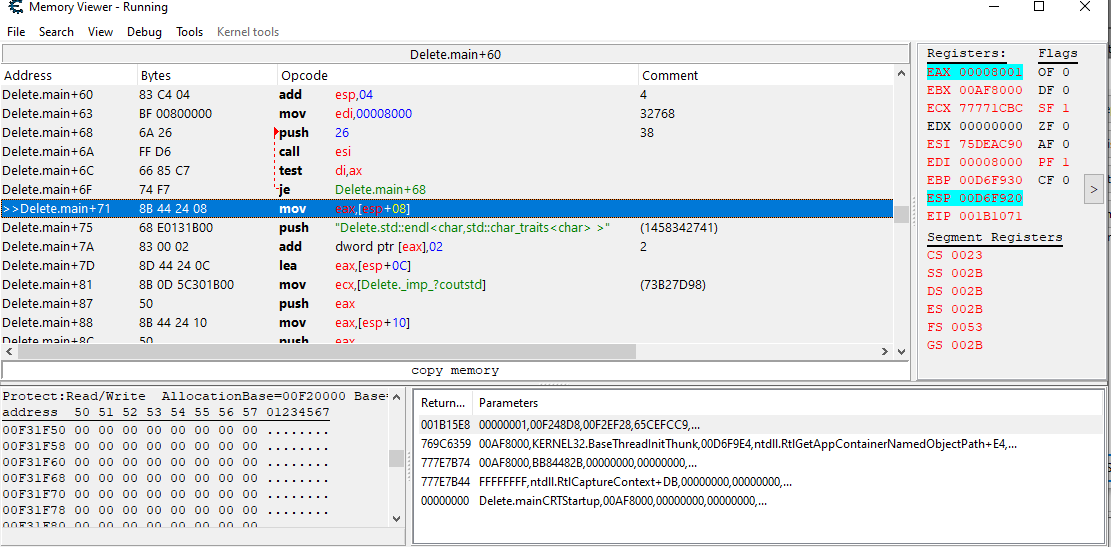
What I did was scanned for the hackableValue as it changed. Then I disassembled the memory region that writes to that address.
Here we can clearly see the
add dword ptr [eax],02
which is where the +2 is added on getAsyncKeystate
and
mov eax,[esp+08]
Which de-references the address (Which is the address where our value is allocated) on ESP + 08 (Meaning that ESP+08 contains the address of the base pointer[I also printed this address in the application itself and the values were equal]). So in our application this would be the address of (&hackableValue).
My question is, how should I go about finding the static offset, from which I can calculate the address(Pointer address) that is assigned to ESP + 08 on each restart of the application.
Thanks in advance for the help.
NOTE:
I attached the images to the post.
| Description: |
|
| Filesize: |
54.59 KB |
| Viewed: |
1861 Time(s) |
|
| Description: |
|
| Filesize: |
33.52 KB |
| Viewed: |
1861 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4695
|
 Posted: Sat Feb 29, 2020 9:15 pm Post subject: Posted: Sat Feb 29, 2020 9:15 pm Post subject: |
 |
|
That isn't how it works. The variable hackableValue is declared inside a function and therefore stored on the stack. Such a pointer can be used as a base address when the game is restarted by using the address of that thread's stack. Look at the function getStackStart in CE's source code here for more information on how to find the address the start of a stack is located at.
If you declare hackableValue outside main (and therefore make it static), subtract its address from the address the exe was loaded at and that will be your offset.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
atom0s
Moderator
 Reputation: 205 Reputation: 205
Joined: 25 Jan 2006
Posts: 8585
Location: 127.0.0.1
|
 Posted: Sun Mar 01, 2020 4:19 am Post subject: Posted: Sun Mar 01, 2020 4:19 am Post subject: |
 |
|
You can't use GetModuleHandle like that from an external process. GetModuleHandle is only for local modules, not for remote ones. You need to use an external means of obtaining the process/module-info such as:
- CreateToolhelp32Snapshot
- Process32First / Process32Next
- Module32First / Module32Next
Or the PSAPI equivalents. (There's a dozen other means to do it depending on if you need to hide/be undetected, etc. but these are the main top-level two.)
_________________
- Retired. |
|
| Back to top |
|
 |
Erik9631
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 24 Aug 2014
Posts: 10
|
 Posted: Sun Mar 01, 2020 6:49 am Post subject: Posted: Sun Mar 01, 2020 6:49 am Post subject: |
 |
|
| ParkourPenguin wrote: | That isn't how it works. The variable hackableValue is declared inside a function and therefore stored on the stack. Such a pointer can be used as a base address when the game is restarted by using the address of that thread's stack. Look at the function getStackStart in CE's source code URL... for more information on how to find the address the start of a stack is located at.
If you declare hackableValue outside main (and therefore make it static), subtract its address from the address the exe was loaded at and that will be your offset. |
Thanks for the reply. The information was very helpful. I have one question however:
What if the variable I would be looking for was located in a thread that would not be the main thread. How would I go about looking for the correct thread?
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4695
|
 Posted: Sun Mar 01, 2020 11:15 am Post subject: Posted: Sun Mar 01, 2020 11:15 am Post subject: |
 |
|
The first few threads will probably be started in a consistent order. If not, use some property of the thread to distinguish it from others. e.g. its start address (ThreadQuerySetWin32StartAddress) or something else in the TEB (wikipedia).
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
|

 Reputation: 152
Reputation: 152 Reputation: 205
Reputation: 205 Reputation: 152
Reputation: 152


