 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
jackzxy
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Jul 2010
Posts: 6
|
 Posted: Sun Nov 27, 2016 2:25 pm Post subject: [Help]Please help, about CustomTypeAutoAssembler Posted: Sun Nov 27, 2016 2:25 pm Post subject: [Help]Please help, about CustomTypeAutoAssembler |
 |
|
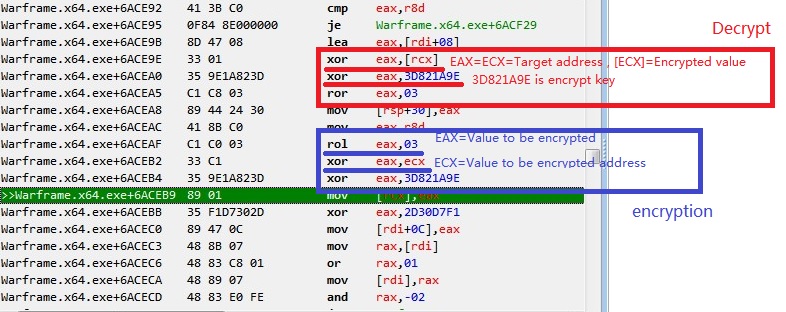
[img]1111.jpg[/img]
Please help me correct my code.
Thx!
my code:
| Code: | registerCustomTypeAutoAssembler([[
alloc(ConvertRoutine,1024)
alloc(ConvertBackRoutine,1024)
alloc(TypeName,256)
alloc(ByteSize,4)
alloc(UsesFloat,1)
alloc(CallMethod,1)
TypeName:
db 'W',0
ByteSize:
dd 4
UsesFloat:
db 0
CallMethod:
db 1
ConvertRoutine:
[32-bit]
push ebp
mov ebp,esp
push ecx
mov ecx,[ebp+8]
[/32-bit]
mov eax,rcx
xor eax,[rcx]
xor eax,3D821A9E
ror eax,03
[64-bit]
ret
[/64-bit]
[32-bit]
pop ecx
pop ebp
ret 4
[/32-bit]
ConvertBackRoutine:
[32-bit]
push ebp
mov ebp,esp
push edx //save the registers
push ecx
mov edx,[ebp+0c]
mov ecx,[ebp+08]
[/32-bit]
push eax
push edx
mov edx,[edx]
mov eax,ecx
rol eax,03
xor eax,rdx
xor eax,3D821A9E
pop edx
mov [edx],eax
pop eax
[64-bit]
ret
[/64-bit]
[32-bit]
//cleanup first
pop ecx
pop edx
pop ebp
ret 8
[/32-bit]
|
| Description: |
|
| Filesize: |
117.88 KB |
| Viewed: |
6427 Time(s) |
|
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Sun Nov 27, 2016 2:39 pm Post subject: Posted: Sun Nov 27, 2016 2:39 pm Post subject: |
 |
|
You need to know the value of RDI for this encryption as well.
Maybe this... | Code: | ConvertRoutine:
[64-bit]
mov eax,edx
xor eax,[rcx]
xor eax,3D821A9E
ror eax,03
ret
[/64-bit] |
| Code: | ConvertBackRoutine:
[64-bit]
rol ecx,03
xor ecx,edx
xor ecx,3D821A9E
mov [r8],ecx
ret
[/64-bit] |
|
|
| Back to top |
|
 |
panraven
Grandmaster Cheater
![]() Reputation: 62 Reputation: 62
Joined: 01 Oct 2008
Posts: 959
|
 Posted: Sun Nov 27, 2016 3:04 pm Post subject: Posted: Sun Nov 27, 2016 3:04 pm Post subject: |
 |
|
<safe...>
When create a new AA custom type in ce 6.6, note the following comment
| Code: |
//The convert routine should hold a routine that converts the data to an integer (in eax)
//function declared as: cdecl int ConvertRoutine(unsigned char *input, PTR_UINT address);
//Note: Keep in mind that this routine can be called by multiple threads at the same time.
ConvertRoutine:
//jmp dllname.functionname
[64-bit]
//or manual:
//parameters: (64-bit)
//rcx=address of input
//rdx=address
mov eax,[rcx] //eax now contains the bytes 'input' pointed to
ret
[/64-bit]
|
The ConvertRoutine is create at CE Memory Space, any normal address reference is on CE memory not target process memory.
The RCX in the CE address is for 1st parameter(unsigned char *input) which is used to read content that copied from target process to ce memory, RDX is for the memory address at Target Process, but to use memory content pointed by RDX at target process, it may need calling ReadProcessMemory inside ConvertRoutine.
In the Lua version, the signature is
| Code: |
function customvaluetype21_bytestovalue(b1,b2,b3,b4,address)
|
The 'address' is the target process memory address. Since Lua can safely read target process memory, it may be easier to do it in Lua version, but expected to be extremely slow.
And, as Zanzer said, it need to know what [rdi+8] is, and if it is possible to access it.
bye~
_________________
- Retarded.
Last edited by panraven on Sun Nov 27, 2016 3:27 pm; edited 1 time in total |
|
| Back to top |
|
 |
jackzxy
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Jul 2010
Posts: 6
|
 Posted: Sun Nov 27, 2016 3:27 pm Post subject: Posted: Sun Nov 27, 2016 3:27 pm Post subject: |
 |
|
| Zanzer wrote: | You need to know the value of RDI for this encryption as well.
Maybe this... | Code: | ConvertRoutine:
[64-bit]
mov eax,edx
xor eax,[rcx]
xor eax,3D821A9E
ror eax,03
ret
[/64-bit] |
| Code: | ConvertBackRoutine:
[64-bit]
rol ecx,03
xor ecx,edx
xor ecx,3D821A9E
mov [r8],ecx
ret
[/64-bit] |
|
At the start of the decryption code, RAX, RCX, RDI+08 are equal.
| Description: |
|
| Filesize: |
294.13 KB |
| Viewed: |
6402 Time(s) |
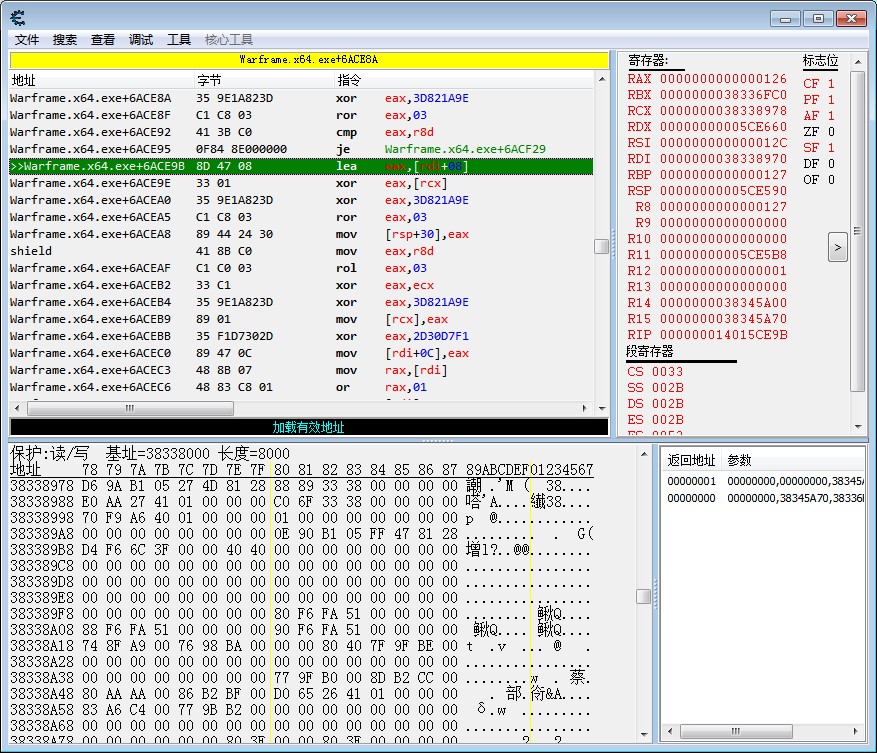
|
|
|
| Back to top |
|
 |
mgr.inz.Player
I post too much
 Reputation: 222 Reputation: 222
Joined: 07 Nov 2008
Posts: 4438
Location: W kraju nad Wisla. UTC+01:00
|
 Posted: Sun Nov 27, 2016 4:21 pm Post subject: Posted: Sun Nov 27, 2016 4:21 pm Post subject: |
 |
|
Analyzing only this piece of code:

We know how encryption (ConvertBackRoutine) is made.
| Code: | alloc(ConvertRoutine,1024)
alloc(ConvertBackRoutine,1024)
alloc(TypeName,256)
alloc(ByteSize,4)
alloc(UsesFloat,1)
alloc(CallMethod,1)
TypeName:
db 'W',0
ByteSize:
dd 4
UsesFloat:
db 0
CallMethod:
db 1
ConvertRoutine:
[64-bit]
mov eax,[rcx]
xor eax,edx
xor eax,3D821A9E
ror eax,03
ret
[/64-bit]
ConvertBackRoutine:
[64-bit]
rol ecx,03
xor ecx,3D821A9E
xor ecx,edx
mov [r8],ecx
ret
[/64-bit] |
for 64bit CallMethod 1
Inside ConvertRoutine function:
rcx - address of buffer (this is a copy)
rdx - address (in target process)
eax - return value
Inside ConvertBackRoutine procedure:
ecx - user input
rdx - address (in target process)
r8 - address of buffer
Edit: Warframe is a multiplayer game. You probably access a copy anyway. I think current shield value is stored on server.
_________________
|
|
| Back to top |
|
 |
jackzxy
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Jul 2010
Posts: 6
|
 Posted: Sun Nov 27, 2016 5:00 pm Post subject: Posted: Sun Nov 27, 2016 5:00 pm Post subject: |
 |
|
| mgr.inz.Player wrote: | Analyzing only this piece of code:
Edit: Warframe is a multiplayer game. You probably access a copy anyway. I think current shield value is stored on server. |
Already made:
Unlimited HP
Unlimited Shield
Unlimited Power
Unlimited Ammo
One Hit Kill
|
|
| Back to top |
|
 |
mgr.inz.Player
I post too much
 Reputation: 222 Reputation: 222
Joined: 07 Nov 2008
Posts: 4438
Location: W kraju nad Wisla. UTC+01:00
|
 Posted: Sun Nov 27, 2016 5:02 pm Post subject: Posted: Sun Nov 27, 2016 5:02 pm Post subject: |
 |
|
"Unlimited HP" - did you test it properly?
_________________
|
|
| Back to top |
|
 |
jackzxy
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Jul 2010
Posts: 6
|
 Posted: Sun Nov 27, 2016 5:18 pm Post subject: Posted: Sun Nov 27, 2016 5:18 pm Post subject: |
 |
|
| mgr.inz.Player wrote: | | "Unlimited HP" - did you test it properly? |
yes
Now I want to find TIME, so I need to decrypt the custom AA
and,Do I understand that right?
| Description: |
|
| Filesize: |
109.31 KB |
| Viewed: |
6302 Time(s) |
|
Last edited by jackzxy on Sun Nov 27, 2016 6:29 pm; edited 3 times in total |
|
| Back to top |
|
 |
mgr.inz.Player
I post too much
 Reputation: 222 Reputation: 222
Joined: 07 Nov 2008
Posts: 4438
Location: W kraju nad Wisla. UTC+01:00
|
 Posted: Sun Nov 27, 2016 5:38 pm Post subject: Posted: Sun Nov 27, 2016 5:38 pm Post subject: |
 |
|
| jackzxy wrote: | | and,Do I understand that right? |
Again:
for 64bit CallMethod 1
Inside ConvertRoutine function:
rcx - address of buffer (this is a copy)
rdx - address (in target process)
eax - return value
Inside ConvertBackRoutine procedure:
ecx - user input
rdx - address (in target process)
r8 - address of buffer
When CE wants to get the value, it has to make a copy of structure at source address, let's say 0x12345678.
So, CE makes a copy from target process to CE Memory, with size defined with ByteSize.
Let's say this buffer is at address 0x00940530 (in CE process, not the target/game process)
ConvertRoutine is called, registers will be:
RCX will be 0x00940530
RDX will be 0x12345678, but, we can not read or write from 0x12345678, because ConvertRoutine works inside CE process, not inside the target/game process.
We set EAX. Function returns EAX value.
Then we see this value in value column.
When CE wants to set the value, again it makes a copy of structure at address let's say 0x12345678.
Let's say this buffer is at address 0x00220530 (again, in CE process, not the target/game process)
ConvertBackRoutine is called, registers will be:
ECX - user value
RDX will be 0x12345678, but, we can not read or write from 0x12345678, because ConvertRoutine works inside CE process, not inside the target/game process.
R8 will be 0x00220530
We do some modifications inside buffer.
This buffer is written back to 0x12345678
_________________
|
|
| Back to top |
|
 |
jackzxy
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Jul 2010
Posts: 6
|
 Posted: Sun Nov 27, 2016 5:48 pm Post subject: Posted: Sun Nov 27, 2016 5:48 pm Post subject: |
 |
|
| mgr.inz.Player wrote: | | jackzxy wrote: | | and,Do I understand that right? |
Again:
for 64bit CallMethod 1
Inside ConvertRoutine function:
rcx - address of buffer (this is a copy)
rdx - address (in target process)
eax - return value
Inside ConvertBackRoutine procedure:
ecx - user input
rdx - address (in target process)
r8 - address of buffer
When CE wants to get the value, it has to make a copy of structure at source address, let's say 0x12345678.
So, CE makes a copy from target process to CE Memory, with size defined with ByteSize.
Let's say this buffer is at address 0x00940530 (in CE process, not the target/game process)
ConvertRoutine is called, registers will be:
RCX will be 0x00940530
RDX will be 0x12345678, but, we can not read or write from 0x12345678, because ConvertRoutine works inside CE process, not inside the target/game process.
We set EAX. Function returns EAX value.
Then we see this value in value column.
When CE wants to set the value, again it makes a copy of structure at address let's say 0x12345678.
Let's say this buffer is at address 0x00220530 (again, in CE process, not the target/game process)
ConvertBackRoutine is called, registers will be:
ECX - user value
RDX will be 0x12345678, but, we can not read or write from 0x12345678, because ConvertRoutine works inside CE process, not inside the target/game process.
R8 will be 0x00220530
We do some modifications inside buffer.
This buffer is written back to 0x12345678 |
Thank you
I understand that you explained it.
Has not been found on the ConvertRoutine information or instructions.
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Sun Nov 27, 2016 5:52 pm Post subject: Posted: Sun Nov 27, 2016 5:52 pm Post subject: |
 |
|
| Did my code not work?
|
|
| Back to top |
|
 |
jackzxy
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 04 Jul 2010
Posts: 6
|
 Posted: Sun Nov 27, 2016 6:10 pm Post subject: Posted: Sun Nov 27, 2016 6:10 pm Post subject: |
 |
|
| Zanzer wrote: | | Did my code not work? |
The result of the decryption is wrong.
But thank you very much for your help.
in game:
address=684AE058
[address]=55C8F3A6
in ConvertRoutine:
address of input:684AE058
rcx=ABA2AE0(Changing)
[rcx]=55C8F3A6
rdx like rcx
Do not know how to read the address of input
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 222
Reputation: 222 Reputation: 222
Reputation: 222 Reputation: 222
Reputation: 222




