 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
7228F43B
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 16 May 2016
Posts: 2
|
 Posted: Mon May 16, 2016 2:53 pm Post subject: Referencing dynamically generated addresses in AA Posted: Mon May 16, 2016 2:53 pm Post subject: Referencing dynamically generated addresses in AA |
 |
|
Hi!
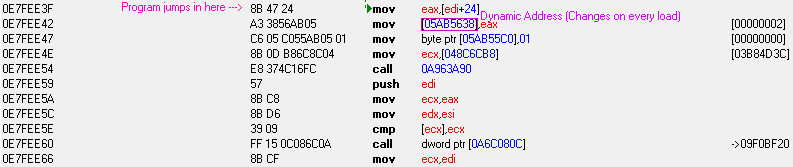
I am trying to write a value of 0xA to the magenta boxed location. (Essentially replacing eax with my value in the second line)
[See attachment (I am not allowed to link it up here yet)]
This is not hard using AA, with for example an aob Injection. However to make it last more than one startup is a problem.
Is it possible to inject code into this segment, using the dynamic address the opcode is referencing here in AA?
| Code: | [ENABLE]
aobscan(INJECT,8B 47 24 A3 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 01 8B ?? ?? ?? ?? ?? E8 ?? ?? ?? ?? 57 8B C8 8B D6 39 09) // should be unique
//--- What I would need -------------------------
define(dynamicAddress, INJECT+4 with length of 5)
//-----------------------------------------------
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
//thus:
mov [dynamicAddress],A
jmp return
INJECT+3:
jmp code
return:
registersymbol(INJECT)
[DISABLE]
INJECT+3:
db A3
INJECT+4:
db dynamicAddress
unregistersymbol(INJECT)
dealloc(newmem) |
db-ing the bytes around the dynamic address was not found to be possible, since the code I was trying to inject was 10 Bytes long and I only have 8 Bytes I am able to replace (first and second opcodes).
| Code: | Bytes to inject:
C7 05 38 56 4D 03 0A 00 00 00
Available:
0E7FEE3F - 8B 47 24 - mov eax,[edi+24]
0E7FEE42 - A3 38566503 - mov [05AB5638],eax { [00000002] }
|
Thank you 
| Description: |
|
| Filesize: |
20.35 KB |
| Viewed: |
3121 Time(s) |
|
|
|
| Back to top |
|
 |
Cake-san
Grandmaster Cheater
 Reputation: 8 Reputation: 8
Joined: 18 Dec 2014
Posts: 541
Location: Semenanjung
|
 Posted: Mon May 16, 2016 3:17 pm Post subject: Posted: Mon May 16, 2016 3:17 pm Post subject: |
 |
|
| Code: |
[ENABLE]
aobscan(_inj,8B 47 24 A3 * * * * C6 05 * * * * 01 8B 0D * * * * E8 * * * * 57)
registersymbol(_inj)
alloc(_temp,8)
_temp:
readmem(_inj,8)
registersymbol(_temp)
alloc(newmem,30)
label(return)
newmem:
mov eax,0A
readmem(_temp+3,5)
jmp return
_inj:
jmp newmem
nop
nop
nop
return:
[DISABLE]
dealloc(newmem)
_inj:
readmem(_temp,8)
unregistersymbol(_inj)
dealloc(_temp)
unregistersymbol(_temp)
|
_________________
... |
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4706
|
 Posted: Mon May 16, 2016 3:49 pm Post subject: Posted: Mon May 16, 2016 3:49 pm Post subject: |
 |
|
| 7228F43B wrote: | | db-ing the bytes around the dynamic address was not found to be possible |
| Code: | [ENABLE]
aobscan(INJECT,8B 47 24 A3 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 01 8B ?? ?? ?? ?? ?? E8 ?? ?? ?? ?? 57 8B C8 8B D6 39 09) // should be unique
registersymbol(INJECT)
INJECT:
db 6A 0A 5A
// push 0A
// pop eax
[DISABLE]
INJECT:
db 8B 47 24
// mov eax,[edi+24]
unregistersymbol(INJECT) |
Think outside the box. You have many other options besides these.
Also, chose a different name for the injection point besides "INJECT". If two scripts use that same symbol, one will override the other, inhibiting it from disabling correctly (i.e. it'll probably crash the process).
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
7228F43B
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 16 May 2016
Posts: 2
|
 Posted: Mon May 16, 2016 4:05 pm Post subject: Posted: Mon May 16, 2016 4:05 pm Post subject: |
 |
|
Thanks alot! 
I got it to work.
I was not aware of the readmem command, nor did I think outside the box. 
| ParkourPenguin wrote: |
Also, choose a different name for the injection point besides "INJECT". If two scripts use that same symbol, one will override the other, inhibiting it from disabling correctly (i.e. it'll probably crash the process).
|
Thanks  I just named "INJECT" for the post, to make it sound less confusing. I just named "INJECT" for the post, to make it sound less confusing.
However I always wondered if having two scripts with the same symbol might lead to collisions.
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 8
Reputation: 8 Reputation: 152
Reputation: 152

