 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
Himsly
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 17 Apr 2016
Posts: 3
|
 Posted: Sun Apr 17, 2016 10:10 pm Post subject: Help to solve OPCODE and AA Posted: Sun Apr 17, 2016 10:10 pm Post subject: Help to solve OPCODE and AA |
 |
|
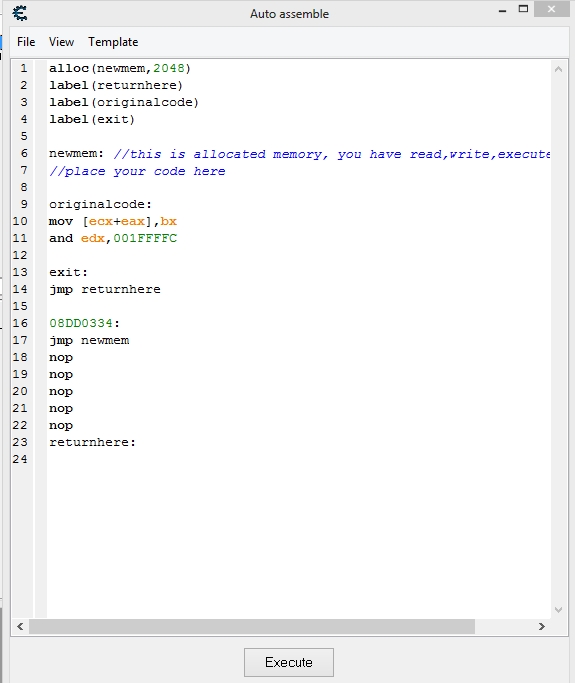
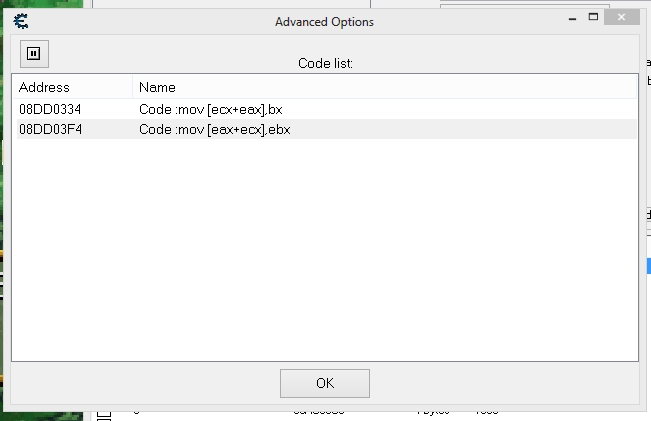
I try to make AA using some Opcode when playing an emulated game Shinobi no Sato no Jintori Gassen (Japan) ISO but it make confuse when there are multiple register on value [], there are eax+ecx, here the code list:
1. mov [eax+ecx],ebx // for player score
2. mov [ecx+eax],bx // for player ball
here is the image on codelist and AA on attachment:
When I add that code there is another address on it inside AA, I mean, "and edx,001FFFFC" on the address, here the code injection:
alloc(newmem,2048)
label(returnhere)
label(originalcode)
label(exit)
newmem: //this is allocated memory, you have read,write,execute access
//place your code here
originalcode:
mov [ecx+eax],bx
and edx,001FFFFC
exit:
jmp returnhere
08DD0334:
jmp newmem
nop
nop
nop
nop
nop
returnhere:
so, my question is,
1. How to deal with multiple register inside the value [], like [ecx+eax]?
2. How to make right code injection based on above AA script? I want to add ball every it decrease?
Thank you so much, Any help will be very appreciated.
| Description: |
|
| Filesize: |
100.02 KB |
| Viewed: |
13358 Time(s) |
|
| Description: |
|
| Filesize: |
54.03 KB |
| Viewed: |
13358 Time(s) |
|
|
|
| Back to top |
|
 |
++METHOS
I post too much
![]() Reputation: 92 Reputation: 92
Joined: 29 Oct 2010
Posts: 4197
|
 Posted: Sun Apr 17, 2016 10:17 pm Post subject: Posted: Sun Apr 17, 2016 10:17 pm Post subject: |
 |
|
You can try this:
| Code: | originalcode:
add [ecx+eax],1
//mov [ecx+eax],bx
and edx,001FFFFC |
But if you're running the game inside of an emulator, then this script will probably not remain reliable. You should use the AOB Injection template.
|
|
| Back to top |
|
 |
Himsly
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 17 Apr 2016
Posts: 3
|
 Posted: Sun Apr 17, 2016 10:26 pm Post subject: Posted: Sun Apr 17, 2016 10:26 pm Post subject: |
 |
|
| ++METHOS wrote: | You can try this:
| Code: | originalcode:
add [ecx+eax],1
//mov [ecx+eax],bx
and edx,001FFFFC |
|
Thank you so much ++METHOS for the code I will try that.
then, my next question is:
1. what is the address "and edx,001FFFFC" mean?
2. how to make right AOB injection script based on that code?
Thank you.
|
|
| Back to top |
|
 |
++METHOS
I post too much
![]() Reputation: 92 Reputation: 92
Joined: 29 Oct 2010
Posts: 4197
|
 Posted: Sun Apr 17, 2016 10:44 pm Post subject: Posted: Sun Apr 17, 2016 10:44 pm Post subject: |
 |
|
1. That is just the instruction below your injection point. It was added as part of the originalcode because of the amount of bytes required for your injection relocation.
2. When you create your script, in the auto assembly window, there should be a template call AOB Injection. Use that and CE will build your script for you, including the AOB. If no unique signature can be found (which is common with emulators), then you'll have to expand on the signature, manually.
|
|
| Back to top |
|
 |
Himsly
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 17 Apr 2016
Posts: 3
|
 Posted: Sun Apr 17, 2016 10:53 pm Post subject: Posted: Sun Apr 17, 2016 10:53 pm Post subject: |
 |
|
| ++METHOS wrote: | You can try this:
| Code: | originalcode:
add [ecx+eax],1
//mov [ecx+eax],bx
and edx,001FFFFC |
But if you're running the game inside of an emulator, then this script will probably not remain reliable. You should use the AOB Injection template. |
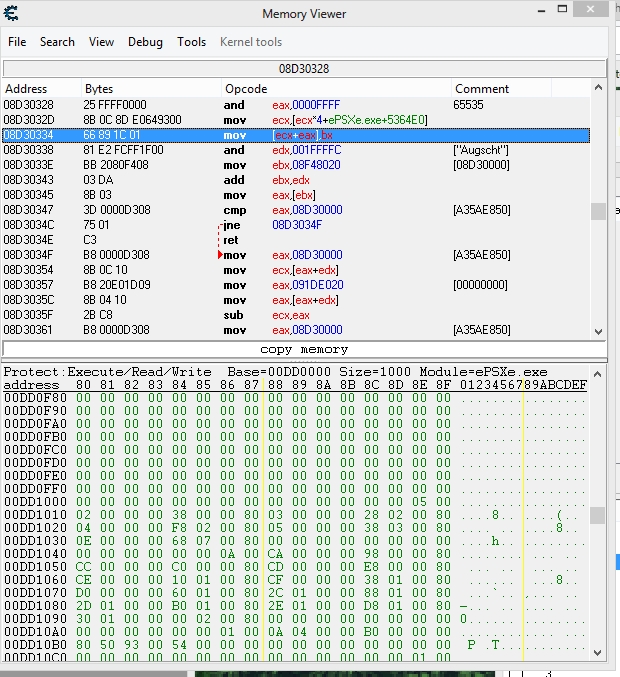
I have try that and got some picture error and the ball is still decrease, here are the pictures:
and the memory is like this on attachment.
so, the unique address is on memory view, then:
1. what the unique address should I take and use based on memory view?
| Description: |
|
| Filesize: |
423.5 KB |
| Viewed: |
13343 Time(s) |
|
| Description: |
|
| Filesize: |
409.28 KB |
| Viewed: |
13343 Time(s) |
|
| Description: |
|
| Filesize: |
403.04 KB |
| Viewed: |
13343 Time(s) |
|
|
|
| Back to top |
|
 |
++METHOS
I post too much
![]() Reputation: 92 Reputation: 92
Joined: 29 Oct 2010
Posts: 4197
|
 Posted: Sun Apr 17, 2016 11:04 pm Post subject: Posted: Sun Apr 17, 2016 11:04 pm Post subject: |
 |
|
Are you sure that you are working from the correct injection point? If you NOP the instruction mov [ecx+eax],bx what happens?
If the desired effect does not play out after NOP'ing the instruction, then perhaps another instruction is writing to the ball address. Since it's an emulator, you'll probably have to filter out addresses, which leads back to your first question:
mov [ecx+eax],bx
In this case, ecx or eax may hold the identifier needed for your filter.
If you've found the address that alters the number of balls (without it resetting back after losing another ball), then right-click on that address to see what is writing to it. Lose two more balls to let the debugger populate. If more than one instruction shows up, then you may need to use multiple injections.
|
|
| Back to top |
|
 |
PinPoint
Expert Cheater
 Reputation: 10 Reputation: 10
Joined: 07 Apr 2016
Posts: 223
Location: Scotland
|
 Posted: Mon Apr 18, 2016 1:46 am Post subject: Posted: Mon Apr 18, 2016 1:46 am Post subject: |
 |
|
| ++METHOS wrote: | Are you sure that you are working from the correct injection point? If you NOP the instruction mov [ecx+eax],bx what happens?
If the desired effect does not play out after NOP'ing the instruction, then perhaps another instruction is writing to the ball address. Since it's an emulator, you'll probably have to filter out addresses, which leads back to your first question:
mov [ecx+eax],bx
In this case, ecx or eax may hold the identifier needed for your filter.
If you've found the address that alters the number of balls (without it resetting back after losing another ball), then right-click on that address to see what is writing to it. Lose two more balls to let the debugger populate. If more than one instruction shows up, then you may need to use multiple injections. |
I'm interested in this also. a few game I've plated on ePSXe have the same format of opcodes and I am unsure of how to do a couple of things. Ive got the naruto game and had a look, the opcodes which write to the addresses in question accesses so many other addresses it slows the game to about 1fps when finding out what the instruction accesses so the crash when you nop it isnt surprising.
using AOB to data for one, for example, adding this to the above script
| Code: | globalalloc(_base1,4) <<<<<<<<<
newmem:
code:
mov [base],eax<<<<<<<<<
mov [eax+ecx],ebx
and edx,001FFFFC
jmp return |
then adding _base1 as a pointer in cheat engine with whatever offset.(ecx in this scenario but it doesnt work)
edit:
the addresses reset -_-. there is only 1 pointer from pointerscan and it resets. even debugger pointer method doesnt work with it
|
|
| Back to top |
|
 |
++METHOS
I post too much
![]() Reputation: 92 Reputation: 92
Joined: 29 Oct 2010
Posts: 4197
|
 Posted: Mon Apr 18, 2016 2:42 am Post subject: Posted: Mon Apr 18, 2016 2:42 am Post subject: |
 |
|
As previously mentioned, in the case of emulators, formats such as [ecx+eax] often contain the ID in one of the registers. You can check to see what the values are for those registers, for the value that you're interested in, then, write a script that will filter out everything except the 'ID' for your target value. This will help you to verify if the filter is valid or not.
Pointerscans, as well as injection (even with AOB), can be tricky with emulators.
| PinPoint wrote: | | Code: | globalalloc(_base1,4) <<<<<<<<<
newmem:
code:
mov [base],eax<<<<<<<<<
mov [eax+ecx],ebx
and edx,001FFFFC
jmp return |
|
-This won't work. First, you need to filter out all of the bad addresses. Then, you need to properly allocate it. For example, you're allocating _base1, but you're using base.
|
|
| Back to top |
|
 |
PinPoint
Expert Cheater
 Reputation: 10 Reputation: 10
Joined: 07 Apr 2016
Posts: 223
Location: Scotland
|
 Posted: Mon Apr 18, 2016 4:59 am Post subject: Posted: Mon Apr 18, 2016 4:59 am Post subject: |
 |
|
sorry, i wrote it wrong on here. this was what i meant
| Code: | globalalloc(_base1,4) <<<<<<<<<
newmem:
code:
mov [_base1],eax<<<<<<<<<
mov [eax+ecx],ebx
and edx,001FFFFC
jmp return |
|
|
| Back to top |
|
 |
++METHOS
I post too much
![]() Reputation: 92 Reputation: 92
Joined: 29 Oct 2010
Posts: 4197
|
 Posted: Mon Apr 18, 2016 2:17 pm Post subject: Posted: Mon Apr 18, 2016 2:17 pm Post subject: |
 |
|
Yes, but you still have to filter out the bad addresses. If you need help with something, just ask. Once you have a reliable filter in place, you can paste your script if you need help with that.
I would start by checking to see what the value is for those two registers [eax+ecx], for your targeted address (balls remaining value?). Once you do that, you can write a filter that will filter out everything that doesn't match. For example...
Let's say that eax holds the address of your targeted value (minus ecx), and ecx holds the ID, which, when added to eax, equals your targeted value. Now, let's say that you find out ecx is 14 for your targeted value. Just write a script that will compare ecx to 14, and if it is, jumps to a section of code that is separate to everything else. In that section of code, you can right-click on it to see what addresses it accesses. If it only accesses your targeted address, then you're good to go; you know that you can use that as an ID for your filter. Once you have the ID, write your script to store the address for future manipulation, without the need to use any traditional pointers.
|
|
| Back to top |
|
 |
PinPoint
Expert Cheater
 Reputation: 10 Reputation: 10
Joined: 07 Apr 2016
Posts: 223
Location: Scotland
|
 Posted: Mon Apr 18, 2016 3:13 pm Post subject: Posted: Mon Apr 18, 2016 3:13 pm Post subject: |
 |
|
| ++METHOS wrote: | Yes, but you still have to filter out the bad addresses. If you need help with something, just ask. Once you have a reliable filter in place, you can paste your script if you need help with that.
I would start by checking to see what the value is for those two registers [eax+ecx], for your targeted address (balls remaining value?). Once you do that, you can write a filter that will filter out everything that doesn't match. For example...
Let's say that eax holds the address of your targeted value (minus ecx), and ecx holds the ID, which, when added to eax, equals your targeted value. Now, let's say that you find out ecx is 14 for your targeted value. Just write a script that will compare ecx to 14, and if it is, jumps to a section of code that is separate to everything else. In that section of code, you can right-click on it to see what addresses it accesses. If it only accesses your targeted address, then you're good to go; you know that you can use that as an ID for your filter. Once you have the ID, write your script to store the address for future manipulation, without the need to use any traditional pointers. |
am i understanding what you mean with this...?
this is the code in the debugger for the opcode writing to the score address
| Code: | 0EA403E8 - 25 FFFF0000 - and eax,0000FFFF
0EA403ED - 8B 0C 8D E0649300 - mov ecx,[ecx*4+ePSXe.exe+5364E0]
0EA403F4 - 89 1C 08 - mov [eax+ecx],ebx <<
0EA403F7 - 81 E2 FCFF1F00 - and edx,001FFFFC
0EA403FD - BB 2000C50E - mov ebx,0EC50020
EAX=0000EB1C
EBX=00000449
ECX=00C379A0
EDX=801EEB1C
ESI=004F7380
EDI=000003E9
ESP=0018FAAC
EBP=0018FF88
EIP=0EA403F7
|
so [eax+ecx]= [0000EB1C+00C379A0] which is correct as the address for score this time is 00C464BC(ePSXe.exe+8464BC)
am I using cmp corrctly in this script?
| Code: | [ENABLE]
aobscan(INJECT,89 1C 08 81 E2 FC FF 1F 00) // should be unique
alloc(compare,$1000)
label(originalcode)
label(return)
compare:
cmp [ecx],00C379A0
//cmp [eax],0000EB1C
jne originalcode
jmp return
originalcode:
mov [eax+ecx],ebx
and edx,001FFFFC
jmp return
INJECT:
jmp compare
nop
nop
nop
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 89 1C 08 81 E2 FC FF 1F 00
unregistersymbol(INJECT)
dealloc(compare) |
the only thing is when I follow the jmp, my compare line changes to -
cmp [ecx],ePSXe.exe+8379A0 so it jumps to the original code.
|
|
| Back to top |
|
 |
++METHOS
I post too much
![]() Reputation: 92 Reputation: 92
Joined: 29 Oct 2010
Posts: 4197
|
 Posted: Mon Apr 18, 2016 4:38 pm Post subject: Posted: Mon Apr 18, 2016 4:38 pm Post subject: |
 |
|
So, in this case, EAX=0000EB1C and ECX=00C379A0.
Since ECX looks like an address and EAX looks more like an offset...EAX may contain your ID, so you'll want to compare against that.
So, you would do something like this:
| Code: | newmem:
cmp eax,EB1C
je @f
jmp originalcode
@@:
mov [eax+ecx],ebx //right-click this instruction to see what addresses are being accessed
and edx,001FFFFC
jmp return
originalcode:
mov [eax+ecx],ebx
and edx,001FFFFC
jmp return |
Right-click the instruction, as shown above. If your ball address is the only thing that shows up, then that can be used as your filter.
|
|
| Back to top |
|
 |
PinPoint
Expert Cheater
 Reputation: 10 Reputation: 10
Joined: 07 Apr 2016
Posts: 223
Location: Scotland
|
 Posted: Mon Apr 18, 2016 4:58 pm Post subject: Posted: Mon Apr 18, 2016 4:58 pm Post subject: |
 |
|
| ++METHOS wrote: | So, in this case, EAX=0000EB1C and ECX=00C379A0.
Since ECX looks like an address and EAX looks more like an offset...EAX may contain your ID, so you'll want to compare against that.
So, you would do something like this:
| Code: | newmem:
cmp eax,EB1C
je @f
jmp originalcode
@@:
mov [eax+ecx],ebx //right-click this instruction to see what addresses are being accessed
and edx,001FFFFC
jmp return
originalcode:
mov [eax+ecx],ebx
and edx,001FFFFC
jmp return |
Right-click the instruction, as shown above. If your ball address is the only thing that shows up, then that can be used as your filter. |
so much stuff is accessed by this also. can I ask what the @f and @@ are in the script you done? havent seen them before
|
|
| Back to top |
|
 |
++METHOS
I post too much
![]() Reputation: 92 Reputation: 92
Joined: 29 Oct 2010
Posts: 4197
|
 Posted: Mon Apr 18, 2016 5:05 pm Post subject: Posted: Mon Apr 18, 2016 5:05 pm Post subject: |
 |
|
If the instruction is accessing many addresses, then you'll have to find a better filter. There are a lot of ways to find a reliable filter. I would start with the other registers:
| Code: | EAX=0000EB1C
EBX=00000449
ECX=00C379A0
EDX=801EEB1C
ESI=004F7380
EDI=000003E9
ESP=0018FAAC
EBP=0018FF88
EIP=0EA403F7 |
EBX or EDI might be good candidates to check out.
If those don't pan out, you can dissect the data structure for your ball address and look for something there.
| Quote: | Anonymous Labels:
FASM supports labels that use no identifier or label name.
@@: represents an anonymous label. Any number of anonymous labels can be defined.
@b refers to the closest @@ that can be found when looking backwards in source. @r and @b are equivalent.
@f refers to the closest @@ that can be found when looking forwards in source. |
-Source.
EDIT:
You need to make sure to set a breakpoint on the instruction in order to get the correct value for eax. You'll have to set up a filter first. You can do something like this:
| Code: | //Target: ePSXe.exe
//Author: ++METHOS
[ENABLE]
{==================== balls ====================}
aobscan(aob_balls,8B0408C325FFFFFF1FXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX15)
alloc(newmem_balls,1024)
label(return_balls)
label(originalcode_balls)
registersymbol(aob_balls)
newmem_balls:
push edi
lea edi,[eax+ecx]
cmp edi,ePSXe.exe+87B260 //////////////change address to current ball address
pop edi
je @f
jmp originalcode_balls
@@:
mov eax,[eax+ecx] //////////////set breakpoint
ret
and eax,1FFFFFFF
jmp return_balls
originalcode_balls:
mov eax,[eax+ecx]
ret
and eax,1FFFFFFF
jmp return_balls
aob_balls:
jmp newmem_balls
db 90 90 90 90
return_balls:
[DISABLE]
dealloc(newmem_balls)
aob_balls:
db 8B 04 08 C3 25 FF FF FF 1F
unregistersymbol(aob_balls) |
In doing so, you will find that eax does, indeed, hold a unique identifier. That said, there appears to be multiple, static addresses that get rotated out for use, so proceeding further may be futile unless you don't mind handling multiple addresses for a single value. Using injection or the pointer scanner will only provide a temporary fix. This is probably due to the fact that it is being emulated. Perhaps someone smarter than me can offer you a solution that I am not aware of.
If you just want to make a table for your own use, I would recommend finding all of the static values that are used for ball quantity. I have no idea if that would even be practical, but it may be your only option here.
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 10
Reputation: 10 Reputation: 10
Reputation: 10 Reputation: 10
Reputation: 10 Reputation: 10
Reputation: 10





