 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
Yuropoor
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Sep 2015
Posts: 10
|
 Posted: Fri Sep 18, 2015 6:01 pm Post subject: Underrail -Too many attribute points cant level up Posted: Fri Sep 18, 2015 6:01 pm Post subject: Underrail -Too many attribute points cant level up |
 |
|
Hello,
^As title states, I have 20 in attribute point, to level up i need to spend the point gained on last level up..
Its too far back to simply load a previous save 
What i want to do is edit my save (either with cheatengine or hex editing) and set one of the attributes to from 20 to 19. I can do the rest from there with cheatengine.
I've tried to use cheatengine to do this by loading a previous save, gaining enuf xp for a level up, alternating by spending 1 and unspending it and using cheatengine to find the right adress, then once found, save the adress and then load my most recent save(the one with 20 in all stats), but it seems that adresses randomly change 
Then i tried HxD, but honestly there seems to be thousands of value differences and the amount of trial and error that would require.. It didnt seem viable.
I'm rather newbie with hex editing and using cheatengine, So i was hoping some here could help me.
Link to archive with two save files; MEGA > #!skgmQLKL!6lh4JJ_OOdJIBVX8gr2bEhSdHo7NFOkwOgWefXUR8CA
( couildnt add attachment and not allowed to post links.. Hope this will not be removed )
Quicksave is the most recent, The one i want to change (set one of the attributes that is currently set to 20 to 19)
1 is the first save, all attributes are set to 10
I'd appreciate any help and/or advice 
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Fri Sep 18, 2015 6:41 pm Post subject: Posted: Fri Sep 18, 2015 6:41 pm Post subject: |
 |
|
Find the address for your ability or the points again.
Right-click and find out what accesses the address.
Select the instruction that pops up and click show disassembler.
Press CTRL-A to open auto assemble and select Template > AOB Injection.
Paste that auto-generated script here.
|
|
| Back to top |
|
 |
Yuropoor
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Sep 2015
Posts: 10
|
 Posted: Fri Sep 18, 2015 6:52 pm Post subject: Posted: Fri Sep 18, 2015 6:52 pm Post subject: |
 |
|
| Zanzer wrote: | Find the address for your ability or the points again.
Right-click and find out what accesses the address.
Select the instruction that pops up and click show disassembler.
Press CTRL-A to open auto assemble and select Template > AOB Injection.
Paste that auto-generated script here. |
'' Right-click and find out what accesses the address. ''
I'm dont know what you mean by this, when searching for Constitution i found two Address.
when disassemble, under opcode, add al,00
What should i do?
3-5 on both of adresses, here are the results;
| Code: | {
{ Game : underrail.exe
Version:
Date : 2015-09-19
Author : Meekaa
This script does blah blah blah
}
[ENABLE]
aobscan(INJECT,04 00 00 00 04 00 00 00 60 36) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
add al,00
add [eax],al
add al,00
jmp return
INJECT:
jmp code
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 04 00 00 00 04 00
unregistersymbol(INJECT)
dealloc(newmem)
// ORIGINAL CODE - INJECTION POINT: 045E6648
045E6636: 00 00 - add [eax],al
045E6638: 0C 5F - or al,5F
045E663A: 60 - pushad
045E663B: 07 - pop es
045E663C: 4C - dec esp
045E663D: 65 5E - pop esi
045E663F: 04 E0 - add al,-20
045E6641: C1 62 04 00 - shl [edx+04],00
045E6645: 00 00 - add [eax],al
045E6647: 00 04 - db 00 04 // SHORTENED TO HIT INJECTION FROM: add [eax+eax],al
// ---------- INJECTING HERE ----------
045E6649: 00 00 - add [eax],al
045E664B: 00 04 00 - add [eax+eax],al
// ---------- DONE INJECTING ----------
045E664E: 00 00 - add [eax],al
045E6650: 60 - pushad
045E6651: 36 4C - dec esp
045E6653: 04 00 - add al,00
045E6655: 00 00 - add [eax],al
045E6657: 00 70 88 - add [eax-78],dh
045E665A: A1 07 38 66 5E - mov eax,[5E663807]
045E665F: 04 00 - add al,00
045E6661: 00 00 - add [eax],al
045E6663: 00 40 E7 - add [eax-19],al
} |
| Code: | { Game : underrail.exe
Version:
Date : 2015-09-19
Author : Meekaa
This script does blah blah blah
}
[ENABLE]
aobscan(INJECT,04 00 00 00 60 36 4C) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
add al,00
add [eax],al
pushad
jmp return
INJECT:
jmp code
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 04 00 00 00 60
unregistersymbol(INJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: 045E664C
045E6638: 0C 5F - or al,5F
045E663A: 60 - pushad
045E663B: 07 - pop es
045E663C: 4C - dec esp
045E663D: 65 5E - pop esi
045E663F: 04 E0 - add al,-20
045E6641: C1 62 04 00 - shl [edx+04],00
045E6645: 00 00 - add [eax],al
045E6647: 00 04 00 - add [eax+eax],al
045E664A: 00 00 - add [eax],al
// ---------- INJECTING HERE ----------
045E664C: 04 00 - add al,00
045E664E: 00 00 - add [eax],al
045E6650: 60 - pushad
// ---------- DONE INJECTING ----------
045E6651: 36 4C - dec esp
045E6653: 04 00 - add al,00
045E6655: 00 00 - add [eax],al
045E6657: 00 70 88 - add [eax-78],dh
045E665A: A1 07 38 66 5E - mov eax,[5E663807]
045E665F: 04 00 - add al,00
045E6661: 00 00 - add [eax],al
045E6663: 00 40 E7 - add [eax-19],al
045E6666: 71 07 - jno 045E666F
045E6668: 00 00 - add [eax],al
} |
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Fri Sep 18, 2015 6:57 pm Post subject: Posted: Fri Sep 18, 2015 6:57 pm Post subject: |
 |
|
Add the address to the table.
Now right-click it.
A fancy menu pops up.
Click Find out what accesses this address.
Or simply select the address and press F5
|
|
| Back to top |
|
 |
Yuropoor
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Sep 2015
Posts: 10
|
 Posted: Fri Sep 18, 2015 7:24 pm Post subject: Posted: Fri Sep 18, 2015 7:24 pm Post subject: |
 |
|
| Zanzer wrote: | Add the address to the table.
Now right-click it.
A fancy menu pops up.
Click Find out what accesses this address.
Or simply select the address and press F5 |
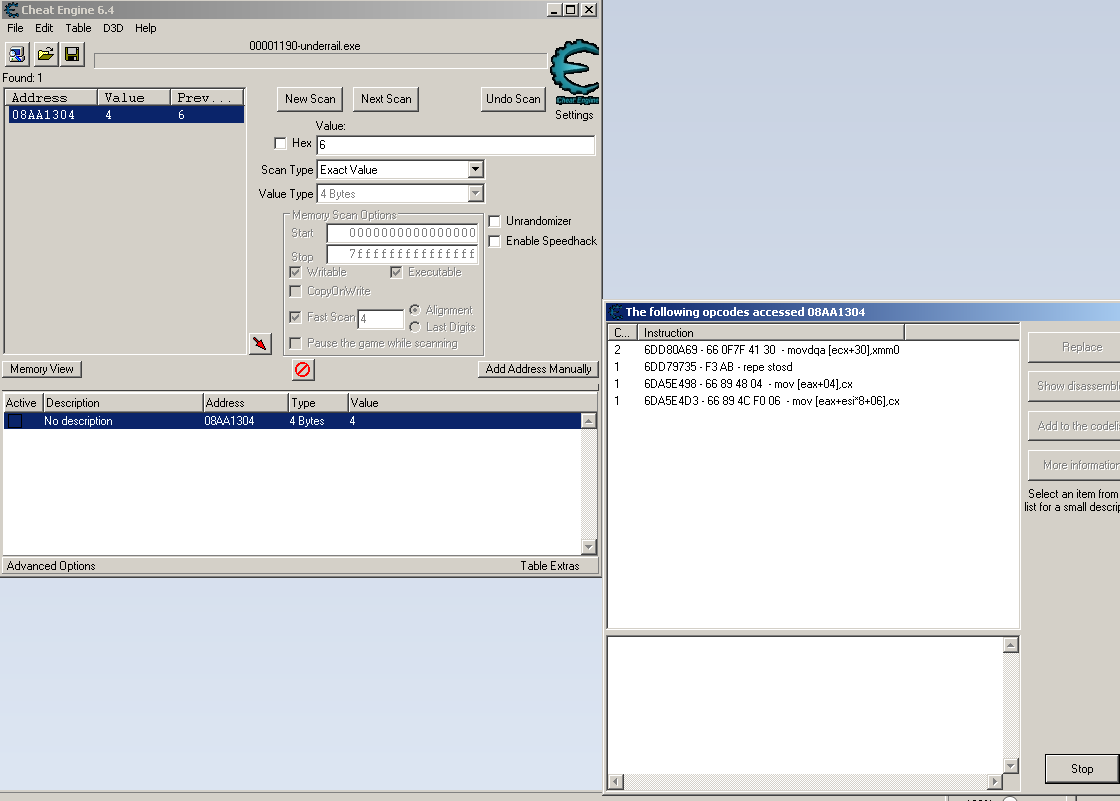
Only one adress this time, 4 instruction
| Code: |
{ Game : underrail.exe
Version:
Date : 2015-09-19
Author : Meekaa
This script does blah blah blah
}
[ENABLE]
aobscanmodule(INJECT,atiumdag.dll,66 0F 7F 41 30) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
movdqa [ecx+30],xmm0
jmp return
INJECT:
jmp code
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 66 0F 7F 41 30
unregistersymbol(INJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: "atiumdag.dll"+4A0A69
"atiumdag.dll"+4A0A4A: 83 E3 0F - and ebx,0F
"atiumdag.dll"+4A0A4D: 85 DB - test ebx,ebx
"atiumdag.dll"+4A0A4F: 75 78 - jne atiumdag.dll+4A0AC9
"atiumdag.dll"+4A0A51: 8B DA - mov ebx,edx
"atiumdag.dll"+4A0A53: 83 E2 7F - and edx,7F
"atiumdag.dll"+4A0A56: C1 EB 07 - shr ebx,07
"atiumdag.dll"+4A0A59: 74 30 - je atiumdag.dll+4A0A8B
"atiumdag.dll"+4A0A5B: 66 0F 7F 01 - movdqa [ecx],xmm0
"atiumdag.dll"+4A0A5F: 66 0F 7F 41 10 - movdqa [ecx+10],xmm0
"atiumdag.dll"+4A0A64: 66 0F 7F 41 20 - movdqa [ecx+20],xmm0
// ---------- INJECTING HERE ----------
"atiumdag.dll"+4A0A69: 66 0F 7F 41 30 - movdqa [ecx+30],xmm0
// ---------- DONE INJECTING ----------
"atiumdag.dll"+4A0A6E: 66 0F 7F 41 40 - movdqa [ecx+40],xmm0
"atiumdag.dll"+4A0A73: 66 0F 7F 41 50 - movdqa [ecx+50],xmm0
"atiumdag.dll"+4A0A78: 66 0F 7F 41 60 - movdqa [ecx+60],xmm0
"atiumdag.dll"+4A0A7D: 66 0F 7F 41 70 - movdqa [ecx+70],xmm0
"atiumdag.dll"+4A0A82: 8D 89 80 00 00 00 - lea ecx,[ecx+00000080]
"atiumdag.dll"+4A0A88: 4B - dec ebx
"atiumdag.dll"+4A0A89: 75 D0 - jne atiumdag.dll+4A0A5B
"atiumdag.dll"+4A0A8B: 85 D2 - test edx,edx
"atiumdag.dll"+4A0A8D: 74 37 - je atiumdag.dll+4A0AC6
"atiumdag.dll"+4A0A8F: 8B DA - mov ebx,edx
} |
| Code: | { Game : underrail.exe
Version:
Date : 2015-09-19
Author : Meekaa
This script does blah blah blah
}
[ENABLE]
aobscanmodule(INJECT,atiumdag.dll,F3 AB 85 D2 74 0A) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
repe stosd
test edx,edx
je atiumdag.dll+499745
jmp return
INJECT:
jmp code
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db F3 AB 85 D2 74 0A
unregistersymbol(INJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: "atiumdag.dll"+499735
"atiumdag.dll"+49971D: 8B C8 - mov ecx,eax
"atiumdag.dll"+49971F: C1 E0 08 - shl eax,08
"atiumdag.dll"+499722: 03 C1 - add eax,ecx
"atiumdag.dll"+499724: 8B C8 - mov ecx,eax
"atiumdag.dll"+499726: C1 E0 10 - shl eax,10
"atiumdag.dll"+499729: 03 C1 - add eax,ecx
"atiumdag.dll"+49972B: 8B CA - mov ecx,edx
"atiumdag.dll"+49972D: 83 E2 03 - and edx,03
"atiumdag.dll"+499730: C1 E9 02 - shr ecx,02
"atiumdag.dll"+499733: 74 06 - je atiumdag.dll+49973B
// ---------- INJECTING HERE ----------
"atiumdag.dll"+499735: F3 AB - repe stosd
"atiumdag.dll"+499737: 85 D2 - test edx,edx
"atiumdag.dll"+499739: 74 0A - je atiumdag.dll+499745
// ---------- DONE INJECTING ----------
"atiumdag.dll"+49973B: 88 07 - mov [edi],al
"atiumdag.dll"+49973D: 83 C7 01 - add edi,01
"atiumdag.dll"+499740: 83 EA 01 - sub edx,01
"atiumdag.dll"+499743: 75 F6 - jne atiumdag.dll+49973B
"atiumdag.dll"+499745: 8B 44 24 08 - mov eax,[esp+08]
"atiumdag.dll"+499749: 5F - pop edi
"atiumdag.dll"+49974A: C3 - ret
"atiumdag.dll"+49974B: 8B 44 24 04 - mov eax,[esp+04]
"atiumdag.dll"+49974F: C3 - ret
"atiumdag.dll"+499750: 55 - push ebp
} |
| Code: | { Game : underrail.exe
Version:
Date : 2015-09-19
Author : Meekaa
This script does blah blah blah
}
[ENABLE]
aobscanmodule(INJECT,atiumdag.dll,66 89 48 04 8B 7B 18) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
mov [eax+04],cx
mov edi,[ebx+18]
jmp return
INJECT:
jmp code
nop
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 66 89 48 04 8B 7B 18
unregistersymbol(INJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: "atiumdag.dll"+17E498
"atiumdag.dll"+17E47D: 8D 46 01 - lea eax,[esi+01]
"atiumdag.dll"+17E480: 83 C4 0C - add esp,0C
"atiumdag.dll"+17E483: 89 47 04 - mov [edi+04],eax
"atiumdag.dll"+17E486: 8B 47 08 - mov eax,[edi+08]
"atiumdag.dll"+17E489: 8D 04 F0 - lea eax,[eax+esi*8]
"atiumdag.dll"+17E48C: EB 08 - jmp atiumdag.dll+17E496
"atiumdag.dll"+17E48E: 56 - push esi
"atiumdag.dll"+17E48F: 8B CF - mov ecx,edi
"atiumdag.dll"+17E491: E8 EA 53 28 00 - call atiumdag.dll+403880
"atiumdag.dll"+17E496: 33 C9 - xor ecx,ecx
// ---------- INJECTING HERE ----------
"atiumdag.dll"+17E498: 66 89 48 04 - mov [eax+04],cx
"atiumdag.dll"+17E49C: 8B 7B 18 - mov edi,[ebx+18]
// ---------- DONE INJECTING ----------
"atiumdag.dll"+17E49F: 3B 37 - cmp esi,[edi]
"atiumdag.dll"+17E4A1: 73 3B - jae atiumdag.dll+17E4DE
"atiumdag.dll"+17E4A3: 8B 4F 04 - mov ecx,[edi+04]
"atiumdag.dll"+17E4A6: 3B F1 - cmp esi,ecx
"atiumdag.dll"+17E4A8: 72 23 - jb atiumdag.dll+17E4CD
"atiumdag.dll"+17E4AA: 8B C6 - mov eax,esi
"atiumdag.dll"+17E4AC: 2B C1 - sub eax,ecx
"atiumdag.dll"+17E4AE: 8D 04 C5 08 00 00 00 - lea eax,[eax*8+00000008]
"atiumdag.dll"+17E4B5: 50 - push eax
"atiumdag.dll"+17E4B6: 8B 47 08 - mov eax,[edi+08]
} |
| Code: | { Game : underrail.exe
Version:
Date : 2015-09-19
Author : Meekaa
This script does blah blah blah
}
[ENABLE]
aobscanmodule(INJECT,atiumdag.dll,66 89 4C F0 06) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
mov [eax+esi*8+06],cx
jmp return
INJECT:
jmp code
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 66 89 4C F0 06
unregistersymbol(INJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: "atiumdag.dll"+17E4D3
"atiumdag.dll"+17E4B9: 6A 00 - push 00
"atiumdag.dll"+17E4BB: 8D 04 C8 - lea eax,[eax+ecx*8]
"atiumdag.dll"+17E4BE: 50 - push eax
"atiumdag.dll"+17E4BF: E8 FC B1 31 00 - call atiumdag.dll+4996C0
"atiumdag.dll"+17E4C4: 8D 46 01 - lea eax,[esi+01]
"atiumdag.dll"+17E4C7: 83 C4 0C - add esp,0C
"atiumdag.dll"+17E4CA: 89 47 04 - mov [edi+04],eax
"atiumdag.dll"+17E4CD: 8B 47 08 - mov eax,[edi+08]
"atiumdag.dll"+17E4D0: 33 C9 - xor ecx,ecx
"atiumdag.dll"+17E4D2: 5F - pop edi
// ---------- INJECTING HERE ----------
"atiumdag.dll"+17E4D3: 66 89 4C F0 06 - mov [eax+esi*8+06],cx
// ---------- DONE INJECTING ----------
"atiumdag.dll"+17E4D8: 5E - pop esi
"atiumdag.dll"+17E4D9: 5B - pop ebx
"atiumdag.dll"+17E4DA: 5D - pop ebp
"atiumdag.dll"+17E4DB: C2 0C 00 - ret 000C
"atiumdag.dll"+17E4DE: 56 - push esi
"atiumdag.dll"+17E4DF: 8B CF - mov ecx,edi
"atiumdag.dll"+17E4E1: E8 9A 53 28 00 - call atiumdag.dll+403880
"atiumdag.dll"+17E4E6: 5F - pop edi
"atiumdag.dll"+17E4E7: 33 C9 - xor ecx,ecx
"atiumdag.dll"+17E4E9: 5E - pop esi
} |
| Description: |
|
| Filesize: |
43.96 KB |
| Viewed: |
17799 Time(s) |
|
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Fri Sep 18, 2015 8:16 pm Post subject: Posted: Fri Sep 18, 2015 8:16 pm Post subject: |
 |
|
Did a different instruction pop up when you closed and opened the profile screen?
You appear to be spending a point in those instructions.
|
|
| Back to top |
|
 |
Yuropoor
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Sep 2015
Posts: 10
|
 Posted: Fri Sep 18, 2015 8:27 pm Post subject: Posted: Fri Sep 18, 2015 8:27 pm Post subject: |
 |
|
| Zanzer wrote: | Did a different instruction pop up when you closed and opened the profile screen?
You appear to be spending a point in those instructions. |
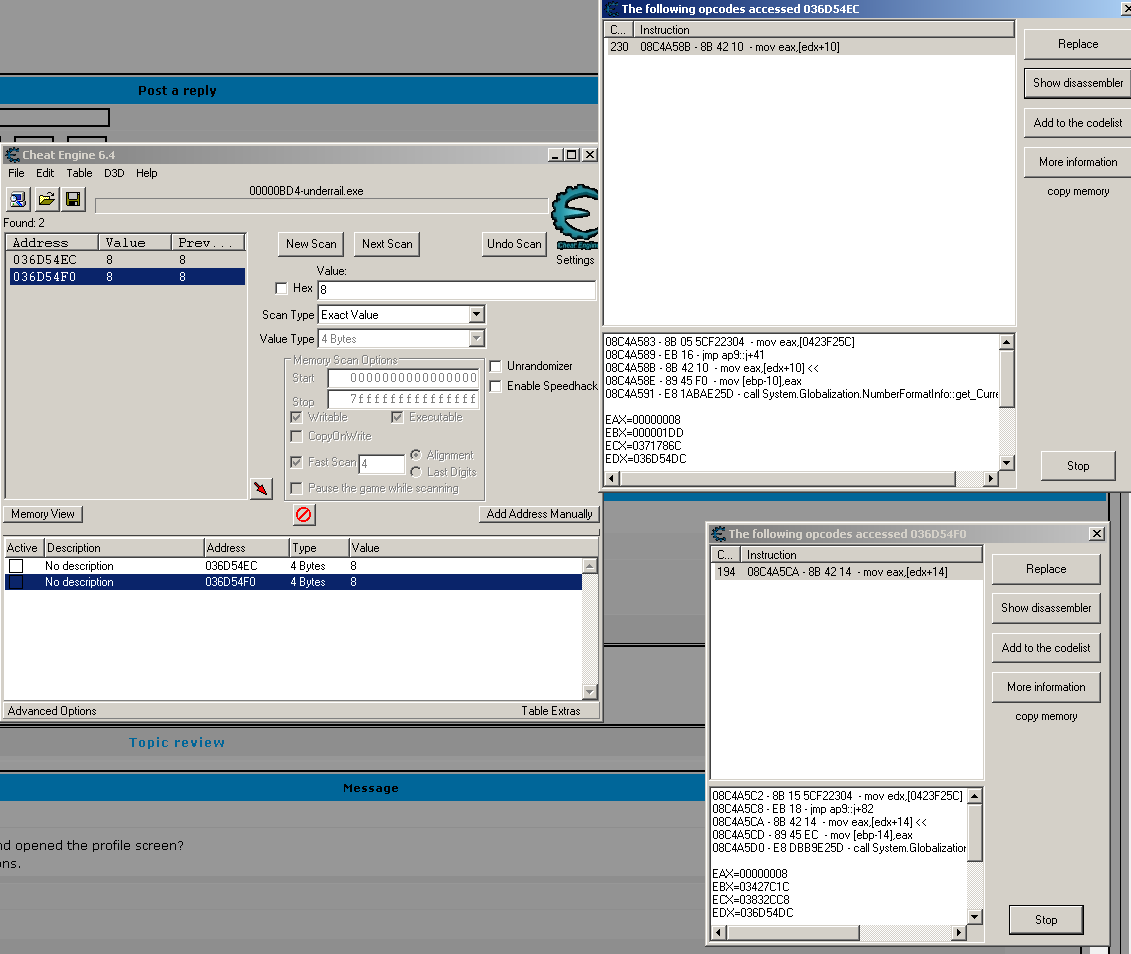
Yes i spent a point because instruction list was empty, when i spent it and looked again, there were a few. Here is a new attempt with no points spent, i only alt+tabbed in and out once
| Code: | { Game : underrail.exe
Version:
Date : 2015-09-19
Author : Meekaa
This script does blah blah blah
}
[ENABLE]
aobscan(INJECT,8B 42 10 89 45 F0 E8) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
mov eax,[edx+10]
mov [ebp-10],eax
jmp return
INJECT:
jmp code
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 8B 42 10 89 45 F0
unregistersymbol(INJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: 08C4A58B
08C4A569: 33 C0 - xor eax,eax
08C4A56B: 89 45 F0 - mov [ebp-10],eax
08C4A56E: 89 45 EC - mov [ebp-14],eax
08C4A571: 8B F1 - mov esi,ecx
08C4A573: 8B BE 6C 01 00 00 - mov edi,[esi+0000016C]
08C4A579: 8B 96 7C 01 00 00 - mov edx,[esi+0000017C]
08C4A57F: 85 D2 - test edx,edx
08C4A581: 75 08 - jne 08C4A58B
08C4A583: 8B 05 5C F2 23 04 - mov eax,[0423F25C]
08C4A589: EB 16 - jmp 08C4A5A1
// ---------- INJECTING HERE ----------
08C4A58B: 8B 42 10 - mov eax,[edx+10]
08C4A58E: 89 45 F0 - mov [ebp-10],eax
// ---------- DONE INJECTING ----------
08C4A591: E8 1A BA E2 5D - call mscorlib.ni.dll+365FB0
08C4A596: 50 - push eax
08C4A597: 8B 4D F0 - mov ecx,[ebp-10]
08C4A59A: 33 D2 - xor edx,edx
08C4A59C: E8 D2 57 B0 5E - call clr.dll+FD73
08C4A5A1: 8B CF - mov ecx,edi
08C4A5A3: 8B D0 - mov edx,eax
08C4A5A5: 39 09 - cmp [ecx],ecx
08C4A5A7: E8 64 38 F1 FE - call 07B5DE10
08C4A5AC: 8B BE 70 01 00 00 - mov edi,[esi+00000170]
} |
| Code: | { Game : underrail.exe
Version:
Date : 2015-09-19
Author : Meekaa
This script does blah blah blah
}
[ENABLE]
aobscan(INJECT,8B 42 14 89 45 EC E8) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
mov eax,[edx+14]
mov [ebp-14],eax
jmp return
INJECT:
jmp code
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 8B 42 14 89 45 EC
unregistersymbol(INJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: 08C4A5CA
08C4A5A3: 8B D0 - mov edx,eax
08C4A5A5: 39 09 - cmp [ecx],ecx
08C4A5A7: E8 64 38 F1 FE - call 07B5DE10
08C4A5AC: 8B BE 70 01 00 00 - mov edi,[esi+00000170]
08C4A5B2: 8B 1D 60 F2 23 04 - mov ebx,[0423F260]
08C4A5B8: 8B 96 7C 01 00 00 - mov edx,[esi+0000017C]
08C4A5BE: 85 D2 - test edx,edx
08C4A5C0: 75 08 - jne 08C4A5CA
08C4A5C2: 8B 15 5C F2 23 04 - mov edx,[0423F25C]
08C4A5C8: EB 18 - jmp 08C4A5E2
// ---------- INJECTING HERE ----------
08C4A5CA: 8B 42 14 - mov eax,[edx+14]
08C4A5CD: 89 45 EC - mov [ebp-14],eax
// ---------- DONE INJECTING ----------
08C4A5D0: E8 DB B9 E2 5D - call mscorlib.ni.dll+365FB0
08C4A5D5: 50 - push eax
08C4A5D6: 8B 4D EC - mov ecx,[ebp-14]
08C4A5D9: 33 D2 - xor edx,edx
08C4A5DB: E8 93 57 B0 5E - call clr.dll+FD73
08C4A5E0: 8B D0 - mov edx,eax
08C4A5E2: FF 35 64 F2 23 04 - push [0423F264]
08C4A5E8: 8B CB - mov ecx,ebx
08C4A5EA: E8 61 E8 E2 5D - call mscorlib.ni.dll+368E50
08C4A5EF: 8B D0 - mov edx,eax
} |
| Description: |
|
| Filesize: |
64.95 KB |
| Viewed: |
17768 Time(s) |
|
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Fri Sep 18, 2015 8:36 pm Post subject: Posted: Fri Sep 18, 2015 8:36 pm Post subject: |
 |
|
When you activate either of these, does the address populate with your points or whatever your address was?
| Description: |
|
Download |
| Filename: |
test.CT |
| Filesize: |
2.37 KB |
| Downloaded: |
1071 Time(s) |
|
|
| Back to top |
|
 |
Yuropoor
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Sep 2015
Posts: 10
|
 Posted: Fri Sep 18, 2015 8:46 pm Post subject: Posted: Fri Sep 18, 2015 8:46 pm Post subject: |
 |
|
| Zanzer wrote: | | When you activate either of these, does the address populate with your points or whatever your address was? |
All my attempts were Constitution adresses, your test seems to show what value Intelligence is.
I determined this by adding 1 point to each attribute individually, making sure to subtract when your test showed no value change. Test does accuratly show Intelligence value when changed.
Before i used cheatengine to determine adress for Con i did remove two points from all the other attributes, not sure if that is related.
I'd prefer con but int is fine i suppose 
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Fri Sep 18, 2015 8:50 pm Post subject: Posted: Fri Sep 18, 2015 8:50 pm Post subject: |
 |
|
If you want, you can simply right-click one of those instructions you found and select:
Find out what addresses this instruction accesses
That should then pop up every single one of your stats and you can do as you please.
|
|
| Back to top |
|
 |
Yuropoor
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Sep 2015
Posts: 10
|
 Posted: Fri Sep 18, 2015 9:06 pm Post subject: Posted: Fri Sep 18, 2015 9:06 pm Post subject: |
 |
|
| Zanzer wrote: | If you want, you can simply right-click one of those instructions you found and select:
Find out what addresses this instruction accesses
That should then pop up every single one of your stats and you can do as you please. |
Seems to work on my save, i can change intelligence value 
By every single of your stats
Do you mean?
| Code: | EAX=038866A4
EBX=036D54EC
ECX=031C0000
EDX=036D5508
ESI=06689BFC
EDI=667185F4
ESP=17D8F070
EBP=17D8F0A8
EIP=678DF9E4 |
Am sure unsure what kind of code i should look for and if/how to apply to to the pointer
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Fri Sep 18, 2015 9:11 pm Post subject: Posted: Fri Sep 18, 2015 9:11 pm Post subject: |
 |
|
If you right-click the instruction and click Find out what address this instruction access
it will show you a listing of every address that instruction accessed...
You can just do that every time you want to change some stats.
|
|
| Back to top |
|
 |
Yuropoor
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Sep 2015
Posts: 10
|
 Posted: Fri Sep 18, 2015 9:15 pm Post subject: Posted: Fri Sep 18, 2015 9:15 pm Post subject: |
 |
|
| Zanzer wrote: | If you right-click the instruction and click Find out what address this instruction access
it will show you a listing of every address that instruction accessed...
You can just do that every time you want to change some stats. |
I understand. Thank you for your help! Thanks to you i dont have to start all over again, I really learnt something here thank you 
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|




