| View previous topic :: View next topic |
| Author |
Message |
SwaggaJackin'
Master Cheater
 Reputation: 2 Reputation: 2
Joined: 06 Nov 2009
Posts: 304
|
 Posted: Sat Jan 07, 2012 9:28 pm Post subject: Confused about this instruction Posted: Sat Jan 07, 2012 9:28 pm Post subject: Confused about this instruction |
 |
|
I'm debugging and stepping through a game and I come across this instruction:
movq [esi+14],xmm0
However, when the instruction is performed [esi+14]'s value never changes despite the fact that xmm0 does contain 2 floating point values:
Here is the state of the game before that instruction is executed with the memory browser set to [esi+14]:

And after the instruction is exected, xmm0 gets cleared and esi+14 remains the same:

Where is the value being copied to if not esi+14? This is confusing me. Thanks.
|
|
| Back to top |
|
 |
Geri
Moderator
![]() Reputation: 112 Reputation: 112
Joined: 05 Feb 2010
Posts: 5627
|
 Posted: Sat Jan 07, 2012 11:20 pm Post subject: Posted: Sat Jan 07, 2012 11:20 pm Post subject: |
 |
|
Did you check other registers? I mean ESI may be a disassembler bug and it is in fact changing EDI+14 or other register. Happens sometimes so it is a possibility. Check if the instruction may change some "other register+14" address. I would start with EDI because esi is usually messed up with edi if it happens.
EDIT:
Also, the debugger is working with the disassembled code so if there is a disassembler error, there will be a debugger error too. So you need to check what was changed "manually" by checking every registers' value +14 before and after the code line is executed.
_________________
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 472 Reputation: 472
Joined: 09 May 2003
Posts: 25880
Location: The netherlands
|
 Posted: Sat Jan 07, 2012 11:49 pm Post subject: Posted: Sat Jan 07, 2012 11:49 pm Post subject: |
 |
|
The other weird thing is that xmm seems to be modified by the instruction. Perhaps the state you see is after the instruction it's currently on has already been executed
What OS and CPU do you use? And how do you step through the code? (F-Keys, debug menu, run till?)
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
SwaggaJackin'
Master Cheater
 Reputation: 2 Reputation: 2
Joined: 06 Nov 2009
Posts: 304
|
 Posted: Sat Jan 07, 2012 11:52 pm Post subject: Posted: Sat Jan 07, 2012 11:52 pm Post subject: |
 |
|
| Geri wrote: | Did you check other registers? I mean ESI may be a disassembler bug and it is in fact changing EDI+14 or other register. Happens sometimes so it is a possibility. Check if the instruction may change some "other register+14" address. I would start with EDI because esi is usually messed up with edi if it happens.
EDIT:
Also, the debugger is working with the disassembled code so if there is a disassembler error, there will be a debugger error too. So you need to check what was changed "manually" by checking every registers' value +14 before and after the code line is executed. |
Alright, I'll check each register in that case and report back when I'm finished.
EDIT:
None of the values at +14 of all the registers changes  . I'm not sure what's going on. I double checked the instructions in IDA . I'm not sure what's going on. I double checked the instructions in IDA
| Code: |
movq qword ptr [esi+14h], xmm0 |
It's the same instruction, so i don't think the disassembler is misinterpreting it.
| Dark Byte wrote: | The other weird thing is that xmm seems to be modified by the instruction. Perhaps the state you see is after the instruction it's currently on has already been executed
What OS and CPU do you use? And how do you step through the code? (F-Keys, debug menu, run till?) |
Windows 7 x64, i5 2500K. Using F7 to step through. I'm using the kernel debugger with DBVM enabled.
|
|
| Back to top |
|
 |
Geri
Moderator
![]() Reputation: 112 Reputation: 112
Joined: 05 Feb 2010
Posts: 5627
|
 Posted: Sun Jan 08, 2012 12:22 am Post subject: Posted: Sun Jan 08, 2012 12:22 am Post subject: |
 |
|
Well you could try something.
1. Make an unknown value scan before the code is executed.
2. Step through the code.
3. Search for changed values.
This may help finding what value is changed by the code.
_________________
|
|
| Back to top |
|
 |
SwaggaJackin'
Master Cheater
 Reputation: 2 Reputation: 2
Joined: 06 Nov 2009
Posts: 304
|
 Posted: Sun Jan 08, 2012 2:01 am Post subject: Posted: Sun Jan 08, 2012 2:01 am Post subject: |
 |
|
| Geri wrote: | Well you could try something.
1. Make an unknown value scan before the code is executed.
2. Step through the code.
3. Search for changed values.
This may help finding what value is changed by the code. |
Unfortunately this isn't working. I guess the address changes each time because it's not finding the values that were in xmm0  . .
Really need to figure this out also. Any other ideas? Thanks.
EDIT:
DarkByte is correct, something strange is occurring.
I used ollydbg for the debugger and it would change the value at ESI +14 correctly and the xmm0 register never got zero'd out.
Tried changing to the 32-bit version of cheat engine, same thing occurs.
What bug is causing this?
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 472 Reputation: 472
Joined: 09 May 2003
Posts: 25880
Location: The netherlands
|
 Posted: Sun Jan 08, 2012 10:54 am Post subject: Posted: Sun Jan 08, 2012 10:54 am Post subject: |
 |
|
Have you tried the VEH or normal windows debugger with that piece of code?
And does olly give the proper results after dbvm has been used to debug at least one process ?
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
SwaggaJackin'
Master Cheater
 Reputation: 2 Reputation: 2
Joined: 06 Nov 2009
Posts: 304
|
 Posted: Sun Jan 08, 2012 11:00 am Post subject: Posted: Sun Jan 08, 2012 11:00 am Post subject: |
 |
|
| Dark Byte wrote: | Have you tried the VEH or normal windows debugger with that piece of code?
And does olly give the proper results after dbvm has been used to debug at least one process ? |
I'll check on the DBVM bit. I am unable to use VEH or WinDBG because the moment I attach the debugger it crashes within 10 seconds, stupid Xlive game (even when using Geri's bypass).
EDIT:
Yes, under DBVM olly still executes it correctly.
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 472 Reputation: 472
Joined: 09 May 2003
Posts: 25880
Location: The netherlands
|
 Posted: Sun Jan 08, 2012 11:08 am Post subject: Posted: Sun Jan 08, 2012 11:08 am Post subject: |
 |
|
Which CE version ?
And if not 6.2 alpha, try http://cheatengine.org/temp/CheatEngine62Alpha3.rar with the veh debugger
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
Geri
Moderator
![]() Reputation: 112 Reputation: 112
Joined: 05 Feb 2010
Posts: 5627
|
 Posted: Sun Jan 08, 2012 11:24 am Post subject: Posted: Sun Jan 08, 2012 11:24 am Post subject: |
 |
|
I can try to check that instruction on my computer if I have that game by accident. I use 32-bit so it is easier for me to mess with debuggers.
_________________
|
|
| Back to top |
|
 |
SwaggaJackin'
Master Cheater
 Reputation: 2 Reputation: 2
Joined: 06 Nov 2009
Posts: 304
|
 Posted: Sun Jan 08, 2012 12:45 pm Post subject: Posted: Sun Jan 08, 2012 12:45 pm Post subject: |
 |
|
I've tried both 6.1 and 6.3 alpha, same result
Geri, check your PM's.
Thanks.
|
|
| Back to top |
|
 |
Geri
Moderator
![]() Reputation: 112 Reputation: 112
Joined: 05 Feb 2010
Posts: 5627
|
 Posted: Sun Jan 08, 2012 11:37 pm Post subject: Posted: Sun Jan 08, 2012 11:37 pm Post subject: |
 |
|
Nah, it is working normally for me. So this is the code:
0052A936 - F3 0F7E 03 - movq xmm0,[ebx]
0052A93A - 66 0FD6 46 14 - movq [esi+14],xmm0
0052A93F - F3 0F7E 43 08 - movq xmm0,[ebx+08]
0052A944 - 66 0FD6 46 1C - movq [esi+1C],xmm0
movq xmm0,[ebx] will copy a float value to xmm0
movq [esi+14],xmm0 will copy that float value to esi+14
movq xmm0,[ebx+08] will copy a new value to xmm0
this will make [ebx] = [esi+14] and it is doing that exactly.
The catch is, that for some reason which I didn't check yet, [esi+14] is equal to [ebx] even before the instruction is executed so it seems that the code is doing nothing, but if I change [esi+14] to 0 and then step in the code, it will be changed back to the value of [ebx].
So the code is working as it should be, though it seems to be somewhat useless at first sight as it is moving a value from one address to another even though they are equal values anyway. I am sure that in some cases, those values are not equal and then it makes sense but at first sight, it can be confusing if you cannot debug it properly because of protections.
EDIT:
Here are 2 pictures from [ebx] in the memory and from [esi+14] in the memory view. Seems pretty much the same. Maybe this instruction is just making sure to make them equal or something.
EDIT 2:
They aren't equal at the start of the level so if you put a breakpoint before the first hit, you will see that [ebx] is a float value and [esi+14] is still 0.
| Description: |
|
| Filesize: |
128.19 KB |
| Viewed: |
12044 Time(s) |
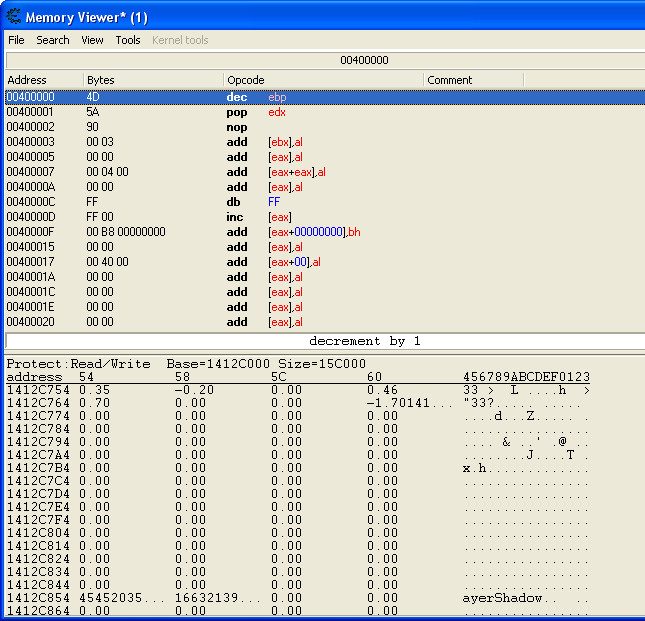
|
| Description: |
|
| Filesize: |
203.91 KB |
| Viewed: |
12044 Time(s) |
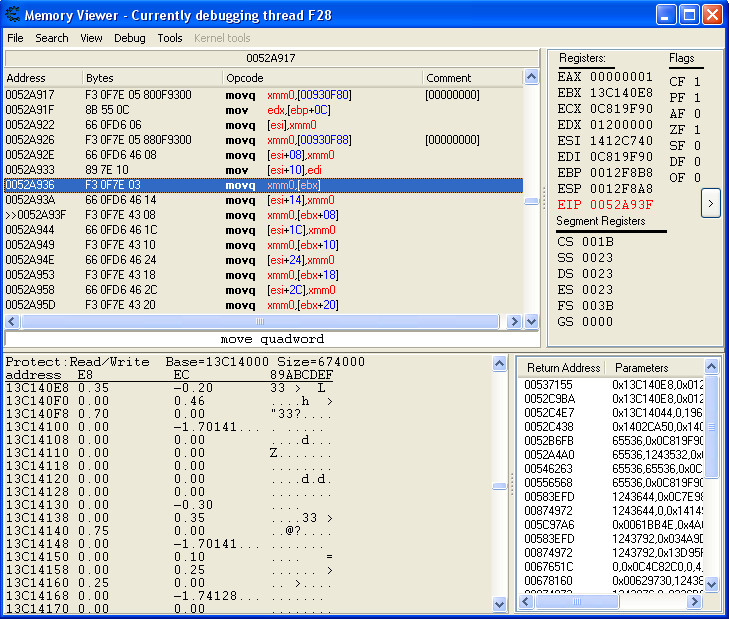
|
_________________
|
|
| Back to top |
|
 |
SwaggaJackin'
Master Cheater
 Reputation: 2 Reputation: 2
Joined: 06 Nov 2009
Posts: 304
|
 Posted: Mon Jan 09, 2012 12:13 am Post subject: Posted: Mon Jan 09, 2012 12:13 am Post subject: |
 |
|
| Why does xmm0 get cleared out though and why does the memory address at ESI+14 never change in my example?
|
|
| Back to top |
|
 |
Geri
Moderator
![]() Reputation: 112 Reputation: 112
Joined: 05 Feb 2010
Posts: 5627
|
 Posted: Mon Jan 09, 2012 12:18 am Post subject: Posted: Mon Jan 09, 2012 12:18 am Post subject: |
 |
|
For me, xmm0 is cleared by the
movq xmm0,[ebx+08]
instruction only.
The movq [esi+14],xmm0 instruction is not changing it.
And the values seems to be equal most of the time, unless you start a new level and set a breakpoint before anything could happen. Before the first hit, [esi+14] is 0. And after that, it is equal to [ebx].
_________________
|
|
| Back to top |
|
 |
SwaggaJackin'
Master Cheater
 Reputation: 2 Reputation: 2
Joined: 06 Nov 2009
Posts: 304
|
 Posted: Mon Jan 09, 2012 2:31 am Post subject: Posted: Mon Jan 09, 2012 2:31 am Post subject: |
 |
|
Well, that's not occurring with me. That sucks because I can't pursue this any further until this gets resolved.
I wonder if it's the OS or the CPU.
|
|
| Back to top |
|
 |
|

 Reputation: 2
Reputation: 2 Reputation: 472
Reputation: 472 Reputation: 2
Reputation: 2 Reputation: 2
Reputation: 2 Reputation: 472
Reputation: 472 Reputation: 2
Reputation: 2 Reputation: 472
Reputation: 472 Reputation: 2
Reputation: 2 Reputation: 2
Reputation: 2 Reputation: 2
Reputation: 2




